AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy, quick to develop, can be really cheap and generally just does what it needs to do.
In general it is considered good practice to not hard code any values into code, functions / methods (depending on your language of choice) but pass values like connection strings, environment names, credentials into the code at runtime, typically via environment variables.
To learn more about Lambda environment variables, read here: https://docs.aws.amazon.com/lambda/latest/dg/configuration-envvars.html
It is also generally considered a good practice to not store any secrets in AWS Lambda environment variables.
Finding Secrets in AWS Lambda Environment
Finding secrets in AWS Lambda environment variables can be achieved via the AWS CLI / PowerShell and generous application of regex or “looking”.
These are the steps to list all your AWS Lambda Functions:
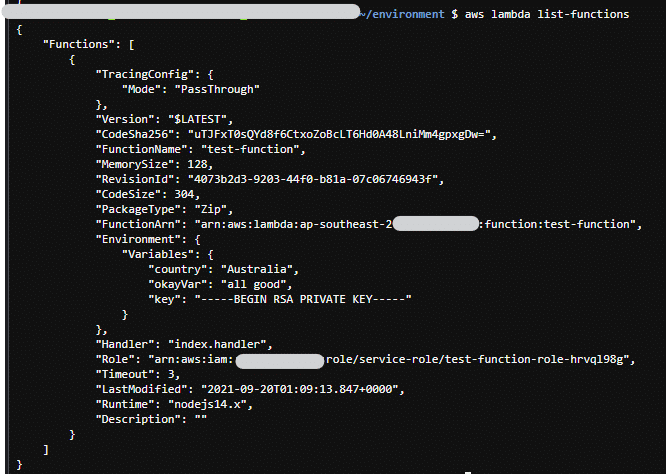
1.
aws lambda list-functions
2. 
3. For each Function you get returned, check each “Environment.Variables” and search for secrets.
4. Repeat this for each AWS Region and AWS Account.
5. We recommend moving those secrets into Systems Manager Parameter Store , AWS Secrets Manager or use a different solution for storing secrets.
Automate Listing Secrets in AWS Lambda
Instead of doing this manually, why not use a service like ARGOS that does this automatically for you?
Identification of this issue is already covered by ARGOS and if set up, ARGOS can send you a message like this into your Slack channel.
If you have not signed up to ARGOS yet then why not spend a few minutes (seriously, minutes!) and sign up to our free trial and see if you have any secrets in your AWS Lambda environment variables.
Sign up at https://argos-security.io