Often customers ask us how they can protect the information stored within ARGOS from individuals that should not have access to it.
Attackers regularly gain access to administrators’ identities and attempt to understand what those identities might have access to. This access more often than not includes third party SaaS products, like ARGOS.
We are already making sure that our customers’ identities are protected by not even storing anything sensitive. ARGOS only supports authentication by Azure Active Directory and GSuite/Gmail users, ensuring that Single Sign-On (SSO) is the default. Multi-factor authentication (MFA) is also supported by default.
Here, however, lies an issue. Over the previous months the industry has become witness to many successful MFA-based attacks on systems, mainly MFA fatigue attacks.
Microsoft Azure has previously attempted to counter some of these attacks by providing users with more information about MFA requests, but this does not prevent successful phishing attempts.
Conditional Authentication Strength
We want our customers to feel that they can protect access to ARGOS as much as possible. With a recent release from Microsoft, they can.
Where some applications might only require SMS based MFA, which can be easily phished, or maybe no MFA at all, a product like ARGOS warrants the highest strength in MFA that is available.
With this new feature (in public preview as of 13/10/2022) our customers can configure access to the ARGOS SaaS application in their Azure tenant to require a “phishing resistant MFA” session.
As part of the regular Azure Entra Conditional Access policy configuration it is now simple to configure different authentication strengths following the official documentation.
We recommend "Phishing resistant multifactor authentication" for access to ARGOS.
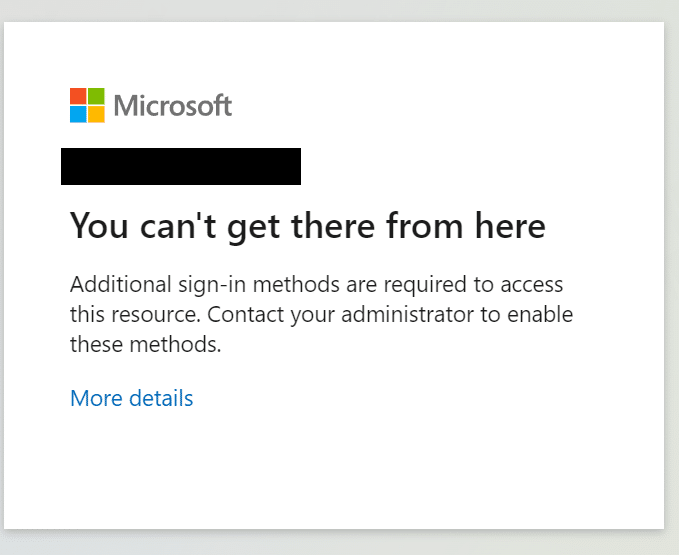
Users that try to log in using weaker MFA methods, like device push or SMS, will receive the following error message.
Looking at the Azure AD sign-in logs you can clearly see why this user’s login attempt was not successful, stating that the “Phishing resistant MFA” requirement was not met.
Flexibility in Security
Microsoft customers, and ARGOS customers alike, have the option to be as flexible in their approach to authentication as their scenarios require.
Need help setting this up or have more questions? Let us know via our contact page, Twitter or our support email.