Azure SQL is a cloud-based relational database management system that is widely used by businesses and organizations around the world. It offers a range of security features to help protect data and prevent unauthorized access, ensuring that sensitive information remains safe and secure.
In this blog post, we will discuss some of the key security features of Azure SQL, and how they can help to enhance data security.
Encryption at Rest and in Transit
One of the most important security features of Azure SQL is encryption. Azure SQL supports encryption at rest and in transit, using industry-standard encryption algorithms such as Advanced Encryption Standard (AES). Encryption at rest ensures that data stored on disk is encrypted, while encryption in transit ensures that data sent between the client and server is encrypted.
Encryption helps to protect data from unauthorized access by ensuring that it is unreadable to anyone without the decryption key. In addition, Azure SQL also supports encryption of backups, providing an additional layer of security.
By default, TDE is enabled for all newly deployed Azure SQL Databases and must be manually enabled for older databases of Azure SQL Database. For Azure SQL Managed Instance, TDE is enabled at the instance level and newly created databases. TDE must be manually enabled for Azure Synapse Analytics.
You can use the following Azure CLI command to find Azure SQL servers that do not have Transparent Data Encryption (TDE) enabled:
az sql server list --query "[?properties.securityEnforcementEnabled==null].{ServerName:name, ResourceGroup:resourceGroup, Location:location}"Example Azure CLI command to enable encryption at rest for an Azure SQL Database:
az sql db tde set --resource-group myResourceGroup --server myServer --database myDatabase --status EnabledFirewall and Virtual Networks
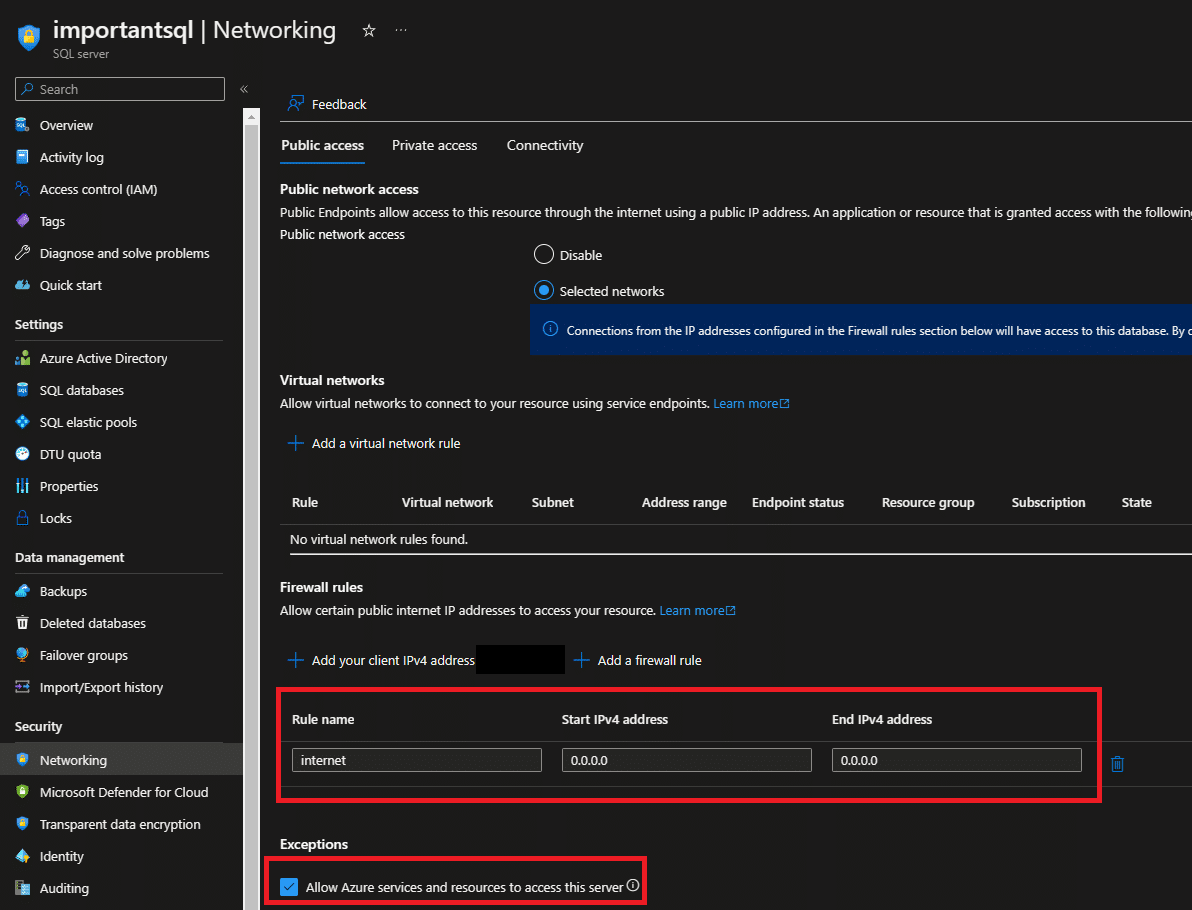
Another key security feature of Azure SQL is the ability to define firewall rules and virtual networks. Firewall rules enable administrators to restrict access to Azure SQL by specifying a range of IP addresses or a specific IP address. This helps to prevent unauthorized access from outside the organization’s network.
Virtual networks, on the other hand, enable administrators to restrict access to Azure SQL to a specific virtual network or subnet within a virtual network. This helps to ensure that only authorized users within the organization can access Azure SQL.
Azure SQL servers now by default don’t allow general public access which is a great improvement from a security point of view. We still see organizations misconfigure the SQL firewall though allowing too much access.
Example Azure CLI command to create a firewall rule to restrict access to an Azure SQL server:
az sql server firewall-rule create --resource-group myResourceGroup --server myServer --name AllowMyIpAddress --start-ip-address 123.123.123.123 --end-ip-address 123.123.123.123Example Azure CLI command to configure a virtual network service endpoint for an Azure SQL server:
az network vnet subnet update --resource-group myResourceGroup --vnet-name myVnet --name mySubnet --service-endpoints Microsoft.SqlAuthentication and Authorization
Azure SQL provides a range of authentication and authorization options to help ensure that only authorized users can access data. Azure SQL supports Azure Active Directory (AAD) authentication, which enables administrators to manage user access and permissions centrally.
If possible, we recommend you use Azure Active Directory authentication for all your use cases.
Example Azure CLI command to enable Azure Active Directory authentication for an Azure SQL server:
az sql server ad-admin create --display-name exampleAdGroup --object-id <objectId> --resource-group myResourceGroup --server myServerAuditing and Threat Detection
Azure SQL provides a range of auditing and threat detection features to help organizations monitor and identify security threats. Azure SQL Auditing enables administrators to monitor database activity, including data access and changes, and identify potential security threats.
Azure SQL Threat Detection provides an additional layer of security by detecting and alerting administrators to potential threats, such as suspicious login attempts or abnormal database activity. This helps organizations to respond quickly to potential security threats and take appropriate action.
Example Azure CLI command to enable auditing for an Azure SQL database and store logs in a Storage Account:
az sql db audit-policy update --resource-group myResourceGroup --server myserver --name mydb --state Enabled --blob-storage-target-state Enabled --storage-account mystorageExample Azure CLI command to enable threat detection for an Azure SQL server and store logs in a Storage Account:
az sql db threat-policy update --resource-group myResourceGroup --server myserver --name mydb --state Enabled --storage-account mystorage
What’s next?
Azure SQL provides a range of security features to help organizations protect their data in the cloud. These features include encryption at rest and in transit, firewall and virtual networks, authentication and authorization, and auditing and threat detection.
By following best practices and configuring these security features appropriately, organizations can help to ensure that their data is secure and protected against potential threats. Using the Azure CLI commands provided in this article, administrators can quickly and easily configure these security features for their Azure SQL databases and servers.
Using ARGOS you can spot the SQL servers and databases that do not comply with above best practices, and ARGOS will also give you the appropriate Azure CLI commands to apply those and increase your compliance and security posture.
Sign up for free and have your first assessment done in the next 5 minutes.