Cloud compliance assessments don’t tell you how you’ll actually be breached.
Cloud infrastructure pentests exist for that exact reason.
Here’s where the difference really matters…
That’s not a criticism of compliance. It’s a distinction we keep blurring.
Most cloud compliance assessments answer a specific thing:
Do these resources align with a standard or benchmark?
They check configurations, validate control presence, and scale well. They’re useful for coverage and assurance.
Cloud infrastructure pentesting starts from a different premise.
It assumes controls exist and asks what happens when they fail.
Attackers don’t operate against benchmarks. They operate against permissions, trust relationships, and identity. That’s where compliance assessments usually stop short.
A typical compliance report returns hundreds of findings. Many valid. Many marked medium or high. Most presented as a flat list.
What’s missing is context.
Those findings rarely explain:
- how an attacker would realistically enter
- how misconfigurations chain together
- which permissions actually matter
- what to fix first, and why
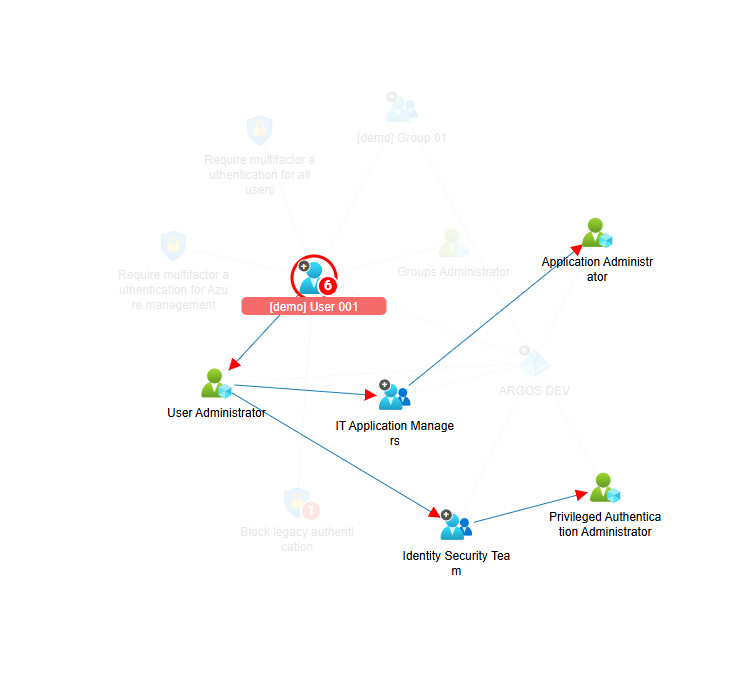
I’ve seen environments that looked largely compliant, yet a single over-permissioned identity enabled lateral movement across subscriptions and access to sensitive workloads in a few steps.
The assessment wasn’t wrong.
It just didn’t model the attack.

Cloud infrastructure pentesting is about modelling that attack and simulating it.
Instead of asking “is this configured correctly?”, the question becomes:
If this is abused, what does it unlock next?
In cloud environments, that means treating identity as the control plane, permissions as the attack surface, and trust as the enabler of movement.
For cloud architects and MSPs, this difference is practical, not academic. You’re asked to assess environments you didn’t design and explain risk to people who want clarity, not another spreadsheet of findings.
That’s also where tooling gets misunderstood.
ARGOS is not a compliance replacement, and it’s not a vulnerability scanner. It supports cloud infrastructure pentesting by making attack paths visible and showing which fixes actually break them.
Compliance tells you whether the doors are locked.
Pentesting shows you which window is open, and where it leads.
Want to test ARGOS for free? Go to https://argos-security.io and register for a free trial.