Dangling DNS records are a real security issue and without going into too much detail as to why this is, here is a quick overview of what “dangling DNS” means in the context of AWS.
If you do want to know more about the in-depth problem of dangling DNS we can highly recommend this paper by the University of Delaware and College of William and Mary.
What is a Dangling DNS Record
In the context of AWS a dangling DNS record means that a Route53 DNS entry (Resource Record) that pointed at an IP address in your cloud exists, but the IP address is not “owned” by you anymore.
As mentioned in our cloud security paper all Cloud Providers make use of well-known IP address ranges and DNS is often publicly enumerable, by design.
Technically this means that anybody can enumerate one’s DNS zone and look for entries that do not successfully resolve anymore. These are usually of the following types:
- A
- CNAME
- MX
- NS
The pattern then continues for the attacker to repeatedly request IP addresses from AWS until at some point the attacker gets lucky and receives the IP of the dangling DNS record. From here on that individual controls that DNS record.
Find AWS Route 53 Dangling Records
AWS currently does not provide any out of the box detection for dangling DNS records in Route 53.

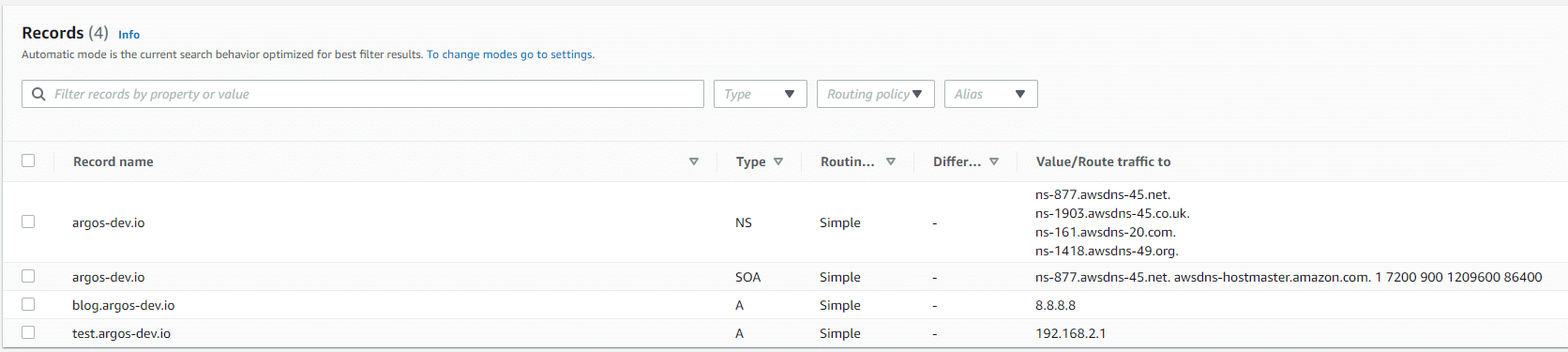
These two entries “test.argos-dev.io” and “blog.argos-dev.io” are both (intentionally) configured as dangling entries. We assume that we have owned those IPs, but nowhere in our environment do we actually have these IPs in our pool. Yes, 8.8.8.8 could technically be seen as a “false positive” because maybe someone really wanted a domain name on top of Google DNS, but let’s ignore that for the purpose of this.
Use AWS CLI to Find Dangling Records
Using the AWS CLI we can automate part of the job to find dangling records. Follow these steps for each AWS Account you own:
- List all Route 53 hosted zones in your AWS Account using “aws route53 list-hosted-zones”. This will return all your zones in Route 53. Take note of the “ID” property.
- For each of your hosted zones, run the following command to list all the IPs that are configured for A records. Repeat this step for CNAME, MX and maybe even NS record types.
aws route53 list-resource-record-sets –hosted-zone-id <yourHostedZoneIdHere> –query “ResourceRecordSets[?Type == ‘A’].ResourceRecords[*].Value[]” - Lastly, let’s check if these addresses actually exist in your environment. For each IP the above returns you need to execute the following command against each of your AWS regions (ideally every single one).
aws ec2 describe-addresses –region us-east-1 –query “Addresses[?PublicIp == ‘8.8.8.8’]”
Automate Detection of AWS Dangling DNS
Instead of doing this manually, why not use a service like ARGOS that does this automatically and continuously for you?
Identification of this issue is already covered by ARGOS and if set up, ARGOS can send you a message like this into your Slack channel.
If you have not signed up to ARGOS yet then why not spend a few minutes (seriously, minutes!) and sign up to our free trial and see if you have any dangling AWS DNS entries in your Route 53.
Sign up at https://argos-security.io