Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker gains access to a single resource within a network and then moves laterally to other resources within the same network. Once an attacker has successfully moved laterally within a network, they can access sensitive data or critical systems.
Network Segmentation
To protect against lateral movement attacks, it’s crucial to implement network segmentation. Network segmentation involves dividing your network into smaller segments, making it more challenging for an attacker to move laterally between resources.
It’s important to note that Azure virtual networks, by default, allow all internal traffic between resources within the same virtual network. This can be a security risk, as it makes it easier for attackers to move laterally within your network and access sensitive data or systems.
To address this, you can configure NSGs to limit traffic between resources within the same virtual network based on specific rules. This can help prevent lateral movement attacks by controlling the flow of traffic between resources.
In addition to NSGs, you can also use Azure Firewall or third-party firewalls to further secure your virtual network. These firewalls can be used to filter traffic based on specific criteria, such as source IP address, destination IP address, or port number.
Overall, implementing network segmentation through the use of NSGs and firewalls is an important step in protecting against lateral movement attacks in the cloud. It’s important to regularly review and update your network security policies to ensure that they remain effective in protecting against evolving threats, including those associated with lateral movement.
Azure Managed Identities
One way to limit the permissions of managed identities is to use RBAC to assign them to roles with only the necessary permissions. You can also use Azure Policy to enforce restrictions on the use of managed identities and prevent them from being used in certain scenarios.
By taking steps to limit user permissions, including the careful management of Azure managed identities, you can help protect your cloud environment from lateral movement attacks. It’s important to regularly review and update your access management policies to ensure that they remain effective in protecting against evolving threats.
Access Management Policies
Limiting user permissions to only those resources and actions that are necessary for their job function is an important best practice for protecting against lateral movement attacks in the cloud. By limiting user permissions, you can help prevent attackers from gaining access to sensitive data or critical systems.
One way to achieve this is through role-based access control (RBAC). RBAC involves assigning users to roles that define the actions and resources they can access within your cloud environment. By assigning users to specific roles based on their job function, you can ensure that they only have access to the resources and actions they need to perform their job duties. This can help prevent attackers from gaining access to resources they don’t need, making it more challenging for them to move laterally within your network.
Strong Authentication Measures
In addition to network segmentation, there are several other best practices for protecting against lateral movement attacks in the cloud. One of the most important is to implement strong authentication measures. This includes multi-factor authentication (MFA) and conditional access policies, which can help prevent attackers from gaining access to your resources even if they manage to obtain a user’s credentials.
Assessing Azure
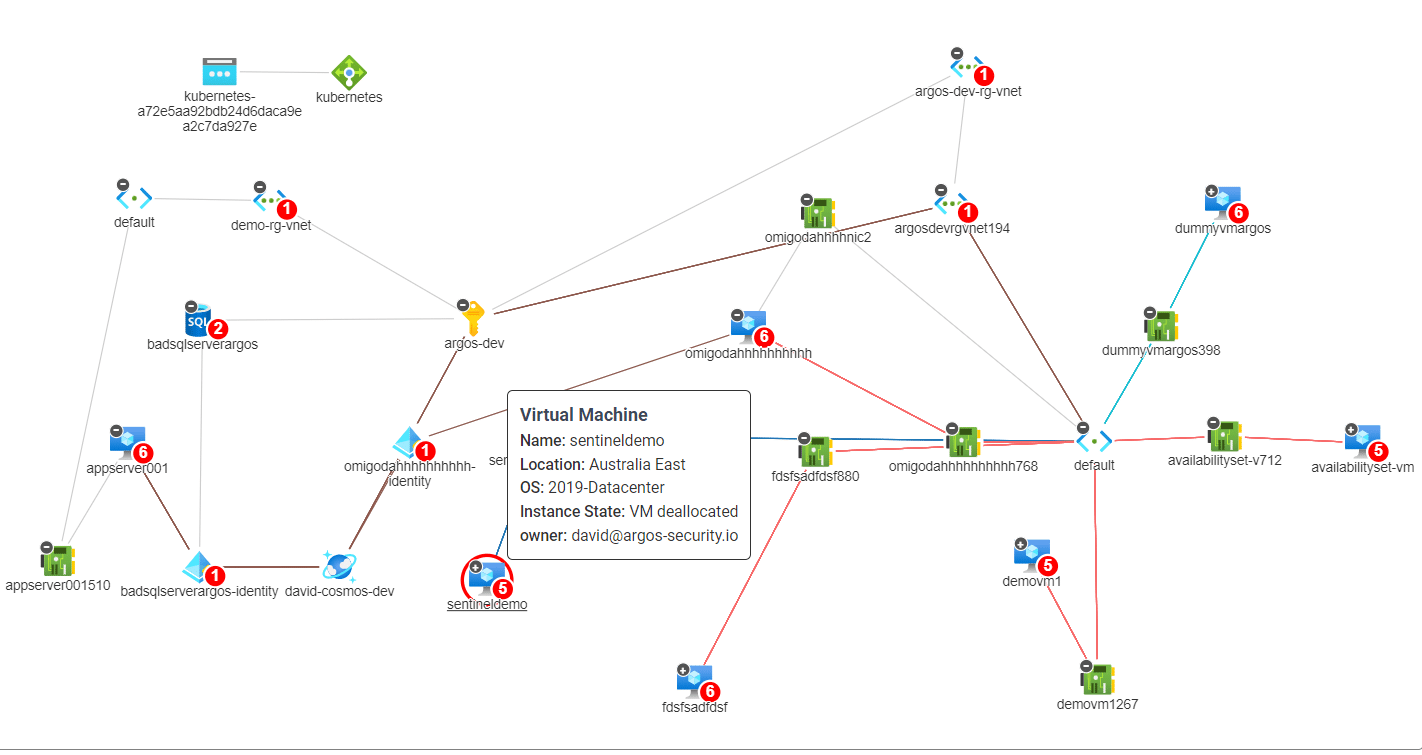
It is important to have the right means and tools available to assess Azure environments with complex architectures and be able to quickly identify and communicate any issues to your colleagues or customers.
If you think a visual representation of the issue would help, one that shows the environmental context and potential lateral movement paths (see coloured lines on below image), then you definitely want to give ARGOS’s free trial a go.
Sign up on https://app.argos-security.io/register .