Top 5 Azure VM Security Blunders that will get you owned
As more and more businesses embrace Azure Virtual Machines (VMs) to scale their IT infrastructure, ensuring the security of these VMs has become a top priority. However, some common security misconfigurations can leave your organization exposed to cyber threats. In this article, we’ll explore the top 5 security misconfigurations of Azure Virtual Machines and provide tips on how to fortify your infrastructure against potential risks.
Inadequate Network Security Group (NSG) Rules
NSGs are virtual firewalls that control both inbound and outbound traffic to your Azure VMs. A common misstep is not setting up these rules properly, which can lead to unauthorized access to your VMs. This is especially the case if the default rules, and their implications, NSGs come with are not fully understood. To avoid this, follow the principle of least privilege, allowing access only to and from essential services and IPs. Regularly review and update your NSG rules to keep them in line with your organization’s security policies.
Default NSG rules can lead to unintentional lateral movement opportunities for attackers, see here.
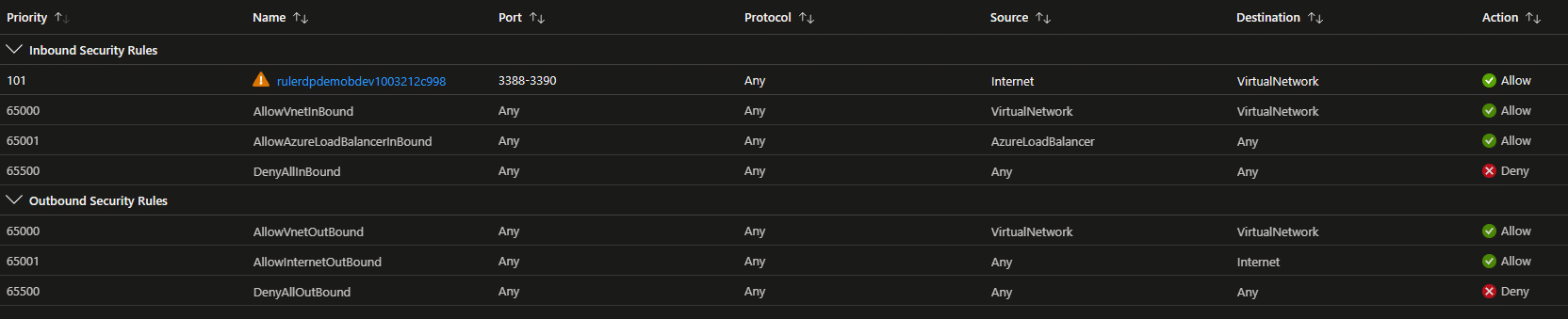
Exposed Management Ports
Leaving management ports like RDP (3389) and SSH (22) exposed to the public internet is a big no-no. Attackers can easily exploit these ports to gain unauthorized access to your VMs. To safeguard against this, restrict access to these ports by configuring NSG rules to allow connections solely from trusted IP addresses. Better yet, use Azure Bastion, a fully managed Azure service that provides secure RDP and SSH connectivity without needing public IP addresses on VMs.
Weak Authentication and Authorization
Relying on weak authentication and authorization mechanisms for your Azure VMs can leave your infrastructure wide open to unauthorized access. This includes using default or weak passwords and not implementing multi-factor authentication (MFA). To strengthen your VMs’ security, use complex and unique passwords, enable MFA for all administrator accounts, and leverage Azure Active Directory (AAD) to manage user access. Implement role-based access control (RBAC) to follow the principle of least privilege.
Further, avoid password authentication on Linux VMs and use SSH authentication.
Better yet, use Azure AD login to Azure VMs. Read more about this for Linux and Windows.
Unencrypted Data Disks
Virtual hard disks (VHDs) used by Azure VMs can become vulnerable to data breaches if not encrypted. Make sure you encrypt both the operating system and data disks to prevent unauthorized access to sensitive information. Azure Disk Encryption (ADE) works in tandem with Azure Key Vault to manage the encryption keys, adding an extra layer of security. Keep your VM disks encrypted and configure your Key Vault to follow the best security practices.
Disabled Monitoring and Logging
Without proper monitoring and logging, security breaches can go undetected, making it challenging to perform effective incident response. To improve visibility and security, enable Azure Monitor and Azure Defender for Cloud to collect and analyze logs, metrics, and diagnostic data from your VMs. Do this by installing the Azure Monitoring Agent (AMA). These tools can help you spot potential security issues and provide recommendations to enhance your infrastructure’s security posture.
Summary
Securing your Azure VMs is an ongoing process that demands vigilance and adherence to best practices. By addressing these top 5 security misconfigurations, you can significantly improve the security posture of your VMs and protect your organization’s valuable assets. Stay on top of your VM configurations and keep yourself informed about the latest security recommendations to ensure your infrastructure remains secure and resilient against evolving cyber threats. Remember, multi-factor authentication is your friend, and keeping track of the context of MFA requests, like Azure MFA Number Matching, can go a long way in safeguarding your infrastructure.
Want to know if your Azure SQL is at risk? Check out this article.
Find Issues Now
Consider signing up for the ARGOS trial to check your first Azure Subscription for free for any of these security issues.