Many teams are confident they have virtual machine access under control. Interactive access is tightly restricted.SSH and RDP are only…
 aws azure cloud infrastructure pentests Cloud security entraid
aws azure cloud infrastructure pentests Cloud security entraid
Why Cloud Infrastructure Pentests Matter
Cloud compliance assessments don’t tell you how you’ll actually be breached.
Cloud infrastructure pentests exist for that exact reason.
Here’s where the difference really matters…
 azure Cloud security
azure Cloud security
Discovering Attack Paths in Microsoft Azure for Enhanced Security
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
Uncovering Lateral Movement Paths in Azure
In the sprawling metropolis of cloud environments, Azure shines as a central hub, teeming with a myriad of services. However, amidst this vast expanse, lurk unseen alleyways known as lateral movement or attack paths, which could be exploited by adversaries to traverse through the cloud undetected.
Common Azure Kubernetes (AKS) Misconfigurations and How to Fix Them
In this article, we will detail the most common AKS misconfigurations, explain their security implications, and provide tips on how to detect and fix them using Azure CLI or Resource Graph examples.
 azure Cloud security
azure Cloud security
Top 5 Azure VM Security Blunders That Get You Owned
Top 5 Azure VM Security Blunders that will get you owned As more and more businesses embrace Azure Virtual Machines…
 azure Cloud security
azure Cloud security
Is Your Azure SQL at Risk? Learn How to Secure It with this Step-by-Step Guide
Azure SQL is a cloud-based relational database management system that is widely used by businesses and organizations around the world.…
 azure Cloud security
azure Cloud security
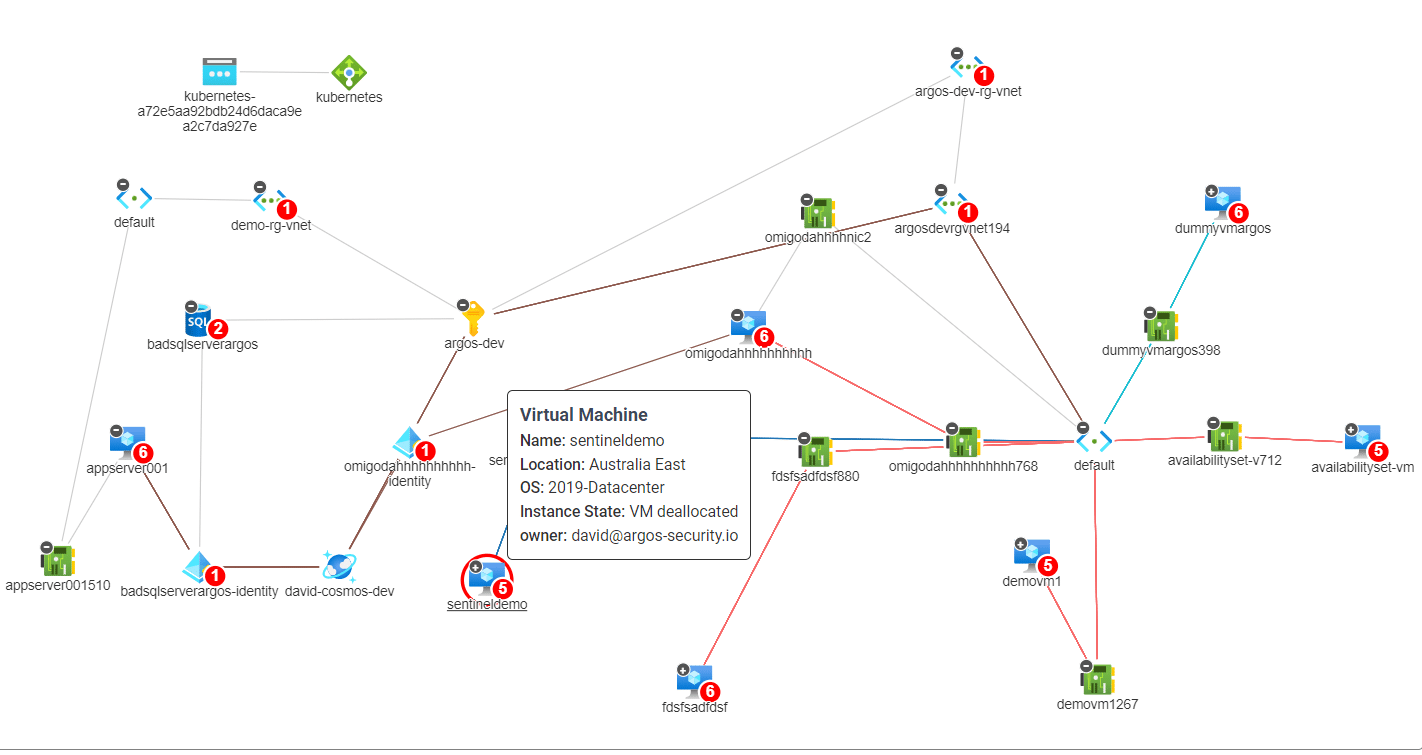
Identifying and Securing Hidden Attack Paths in Azure Infrastructure
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 Cloud security Start up
Cloud security Start up
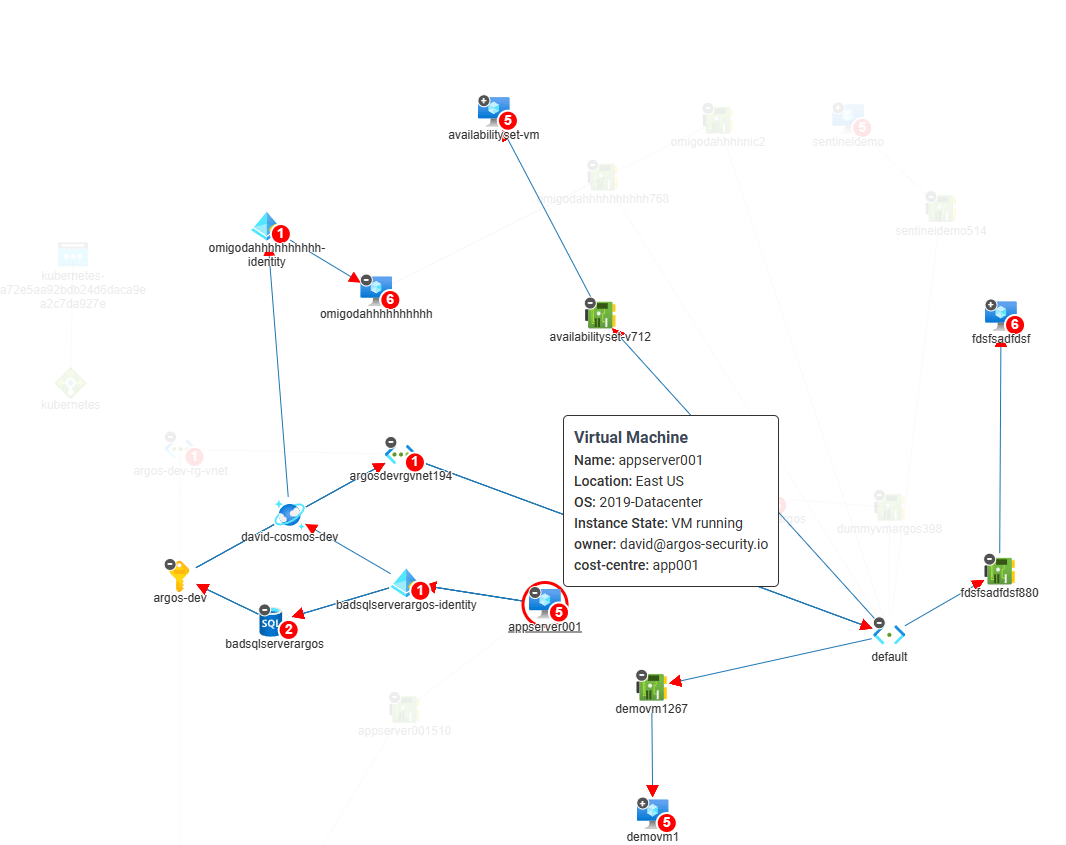
Why We Started ARGOS – Cloud Security FOR Consultants
Today, we wanted to give you a little history lesson into why we started ARGOS. What lead us to build…
 azure Cloud security
azure Cloud security
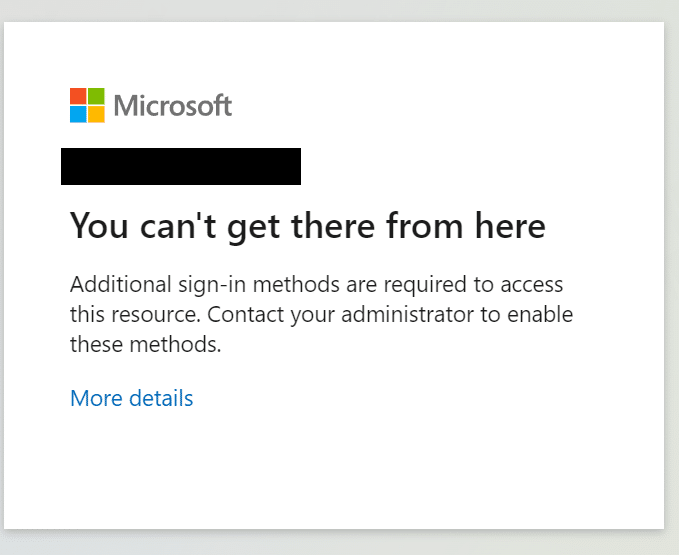
How to protect SaaS with Strong Azure MFA Authentication
Often customers ask us how they can protect the information stored within ARGOS from individuals that should not have access…
