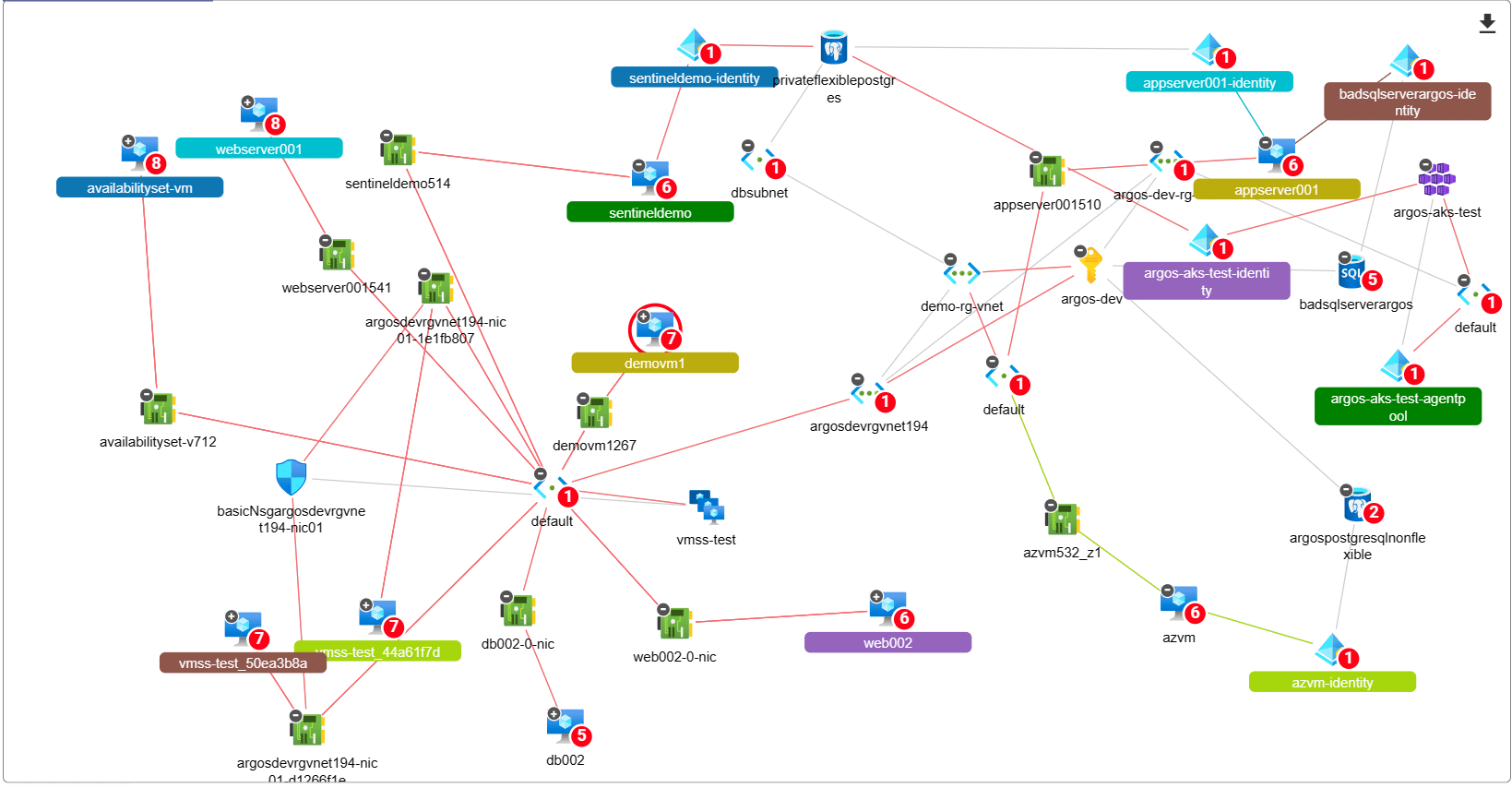
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
 azure Cloud security
azure Cloud security
 azure Cloud security
azure Cloud security
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
 azure Cloud security
azure Cloud security
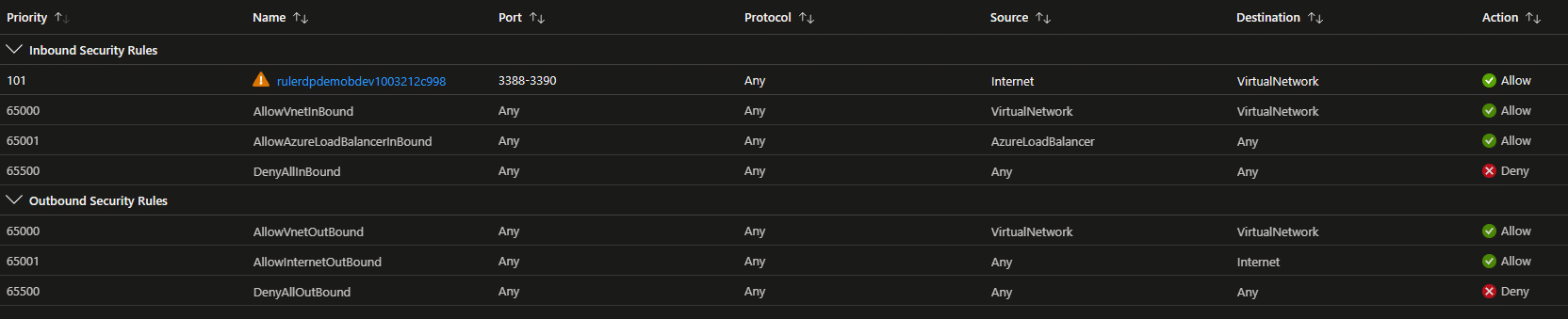
Top 5 Azure VM Security Blunders that will get you owned As more and more businesses embrace Azure Virtual Machines…
 azure Cloud security
azure Cloud security
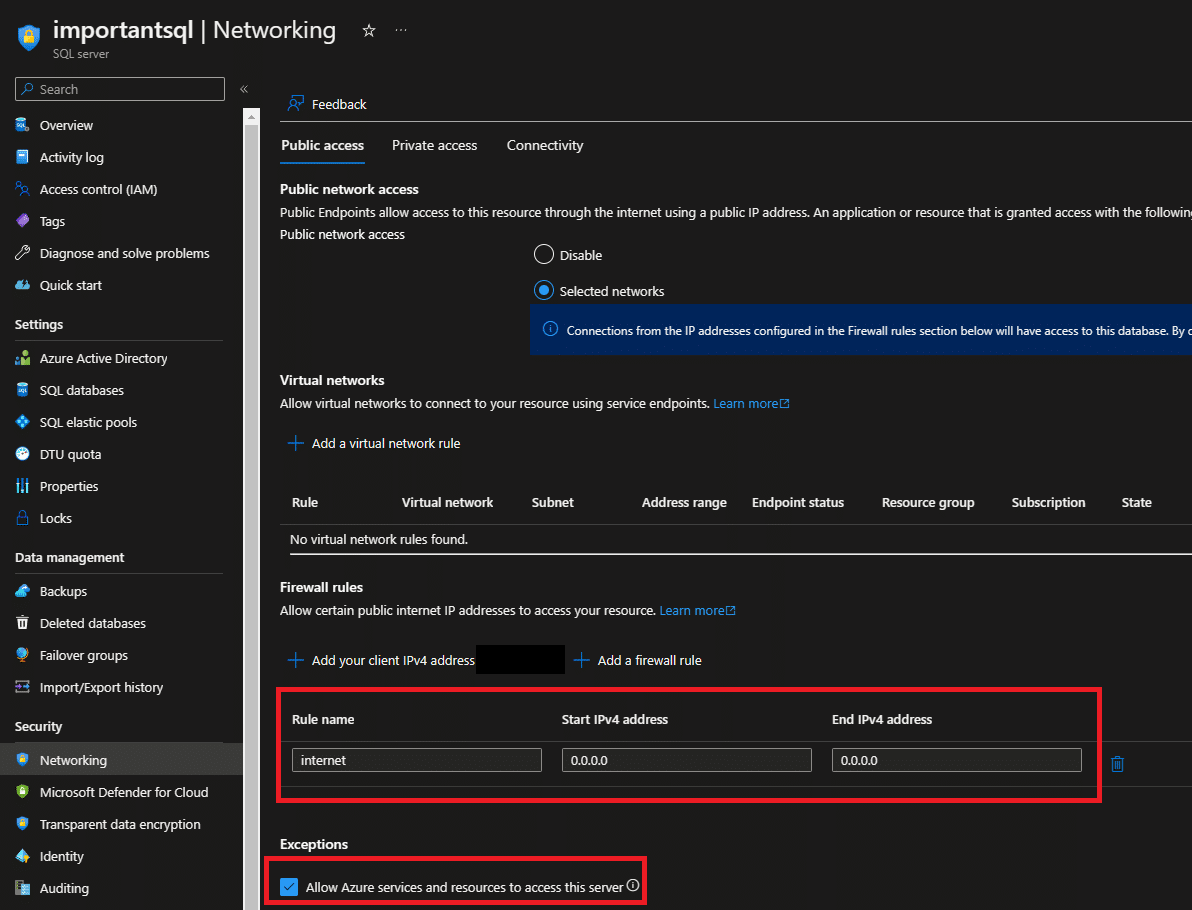
Azure SQL is a cloud-based relational database management system that is widely used by businesses and organizations around the world.…
 azure Cloud security
azure Cloud security
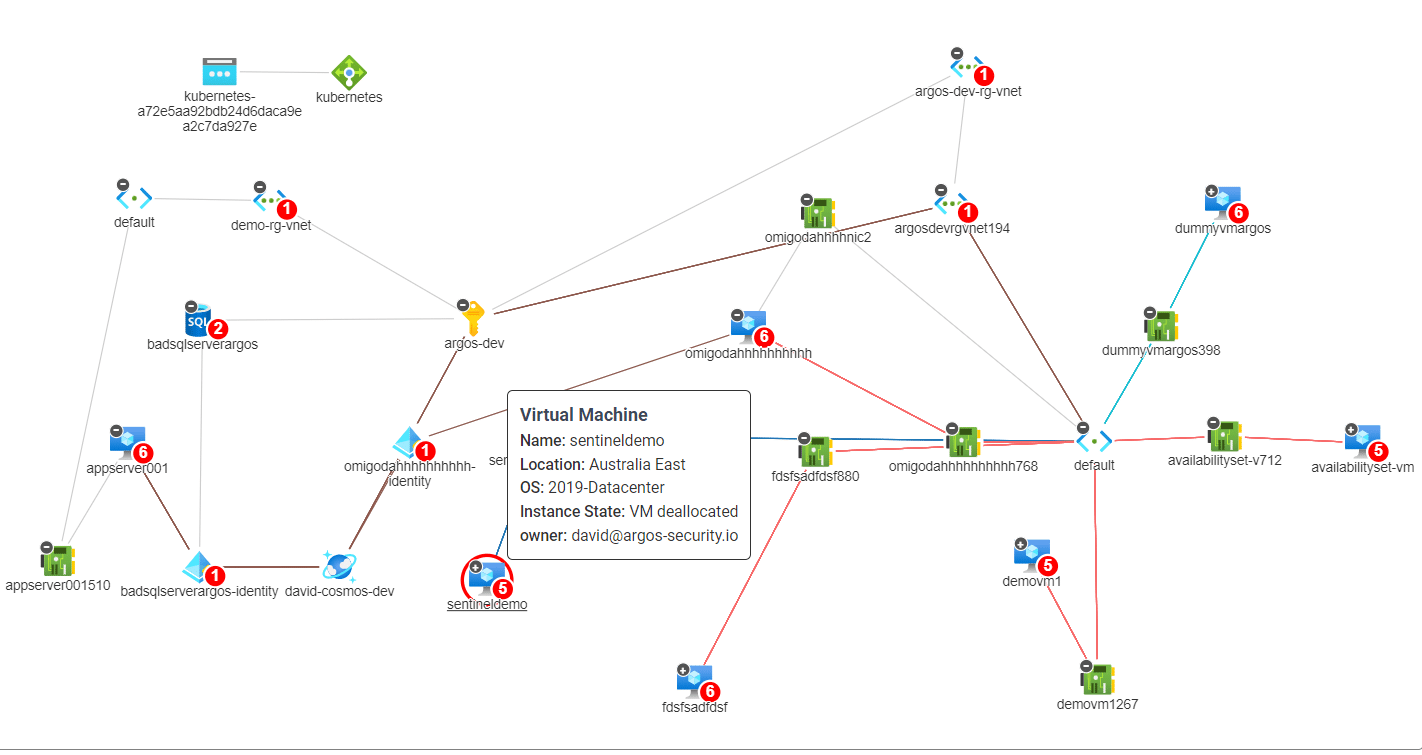
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 aws Cloud security
aws Cloud security
Amazon Web Services (AWS) Identity and Access Management (IAM) is one of the things that is often, let’s say, overly…
