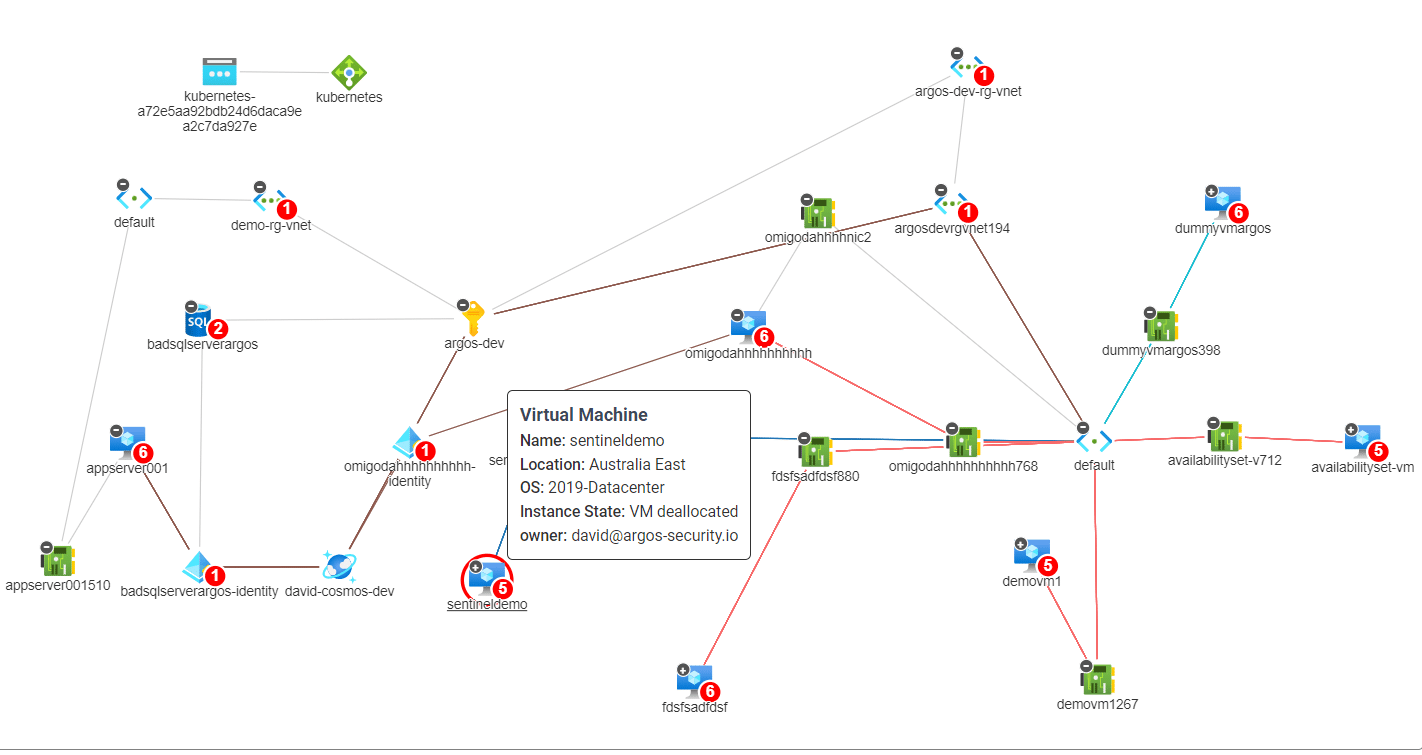
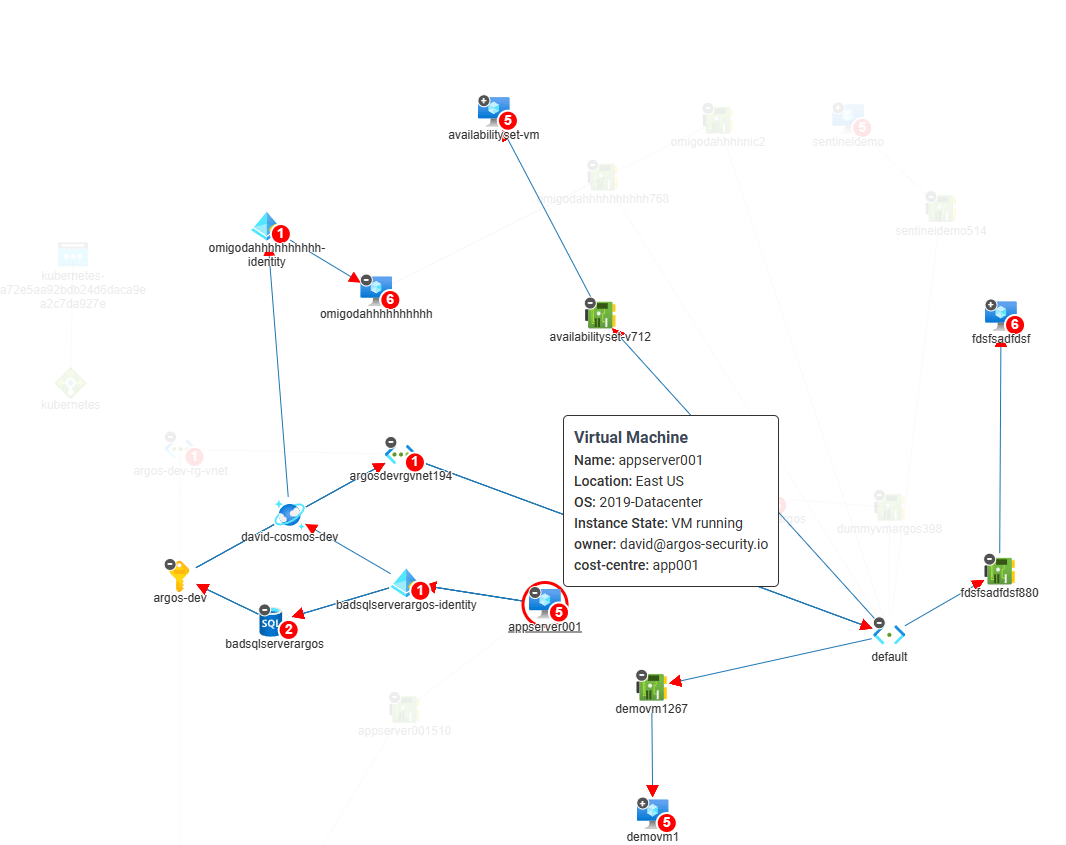
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 azure Cloud security
azure Cloud security
 azure Cloud security
azure Cloud security
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 Cloud security Start up
Cloud security Start up
Today, we wanted to give you a little history lesson into why we started ARGOS. What lead us to build…
 azure Cloud security
azure Cloud security
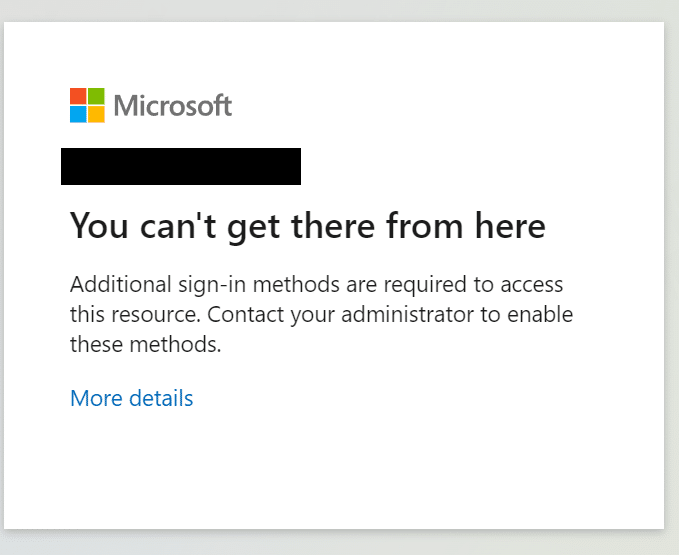
Often customers ask us how they can protect the information stored within ARGOS from individuals that should not have access…
Did you come here because you typed “What is CSPM” or “Do I need a CIEM?” into the search engine?…
 aws Cloud security
aws Cloud security
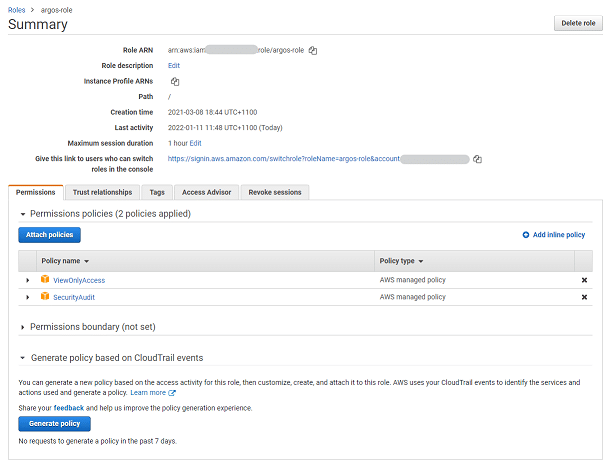
Amazon Web Services (AWS) Identity and Access Management (IAM) is one of the things that is often, let’s say, overly…
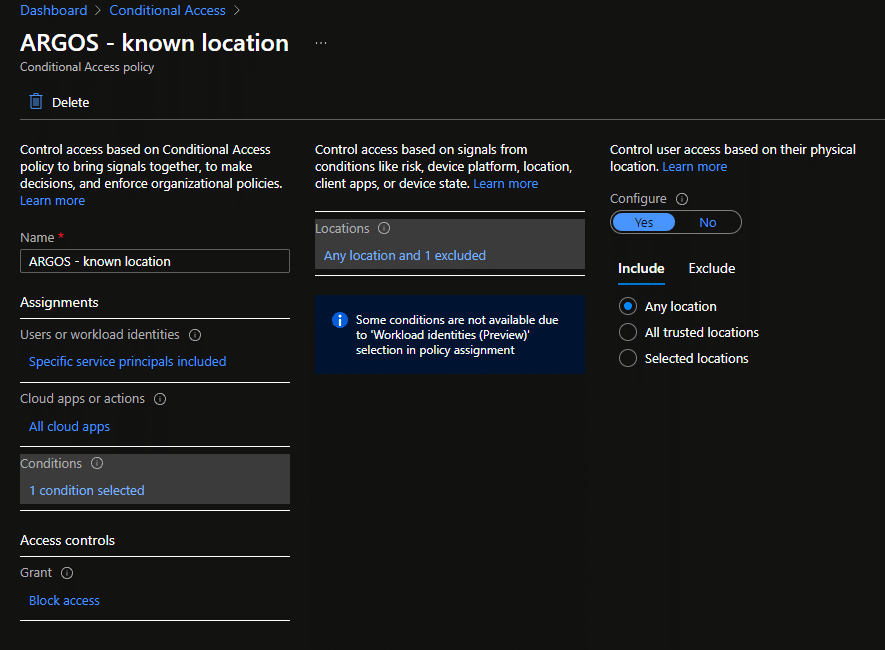 azure Cloud security Devsecops
azure Cloud security Devsecops
Identity and Access Management (IAM) is absolutely fundamental to a Cloud operation, however, sometimes you had to make allowances for…
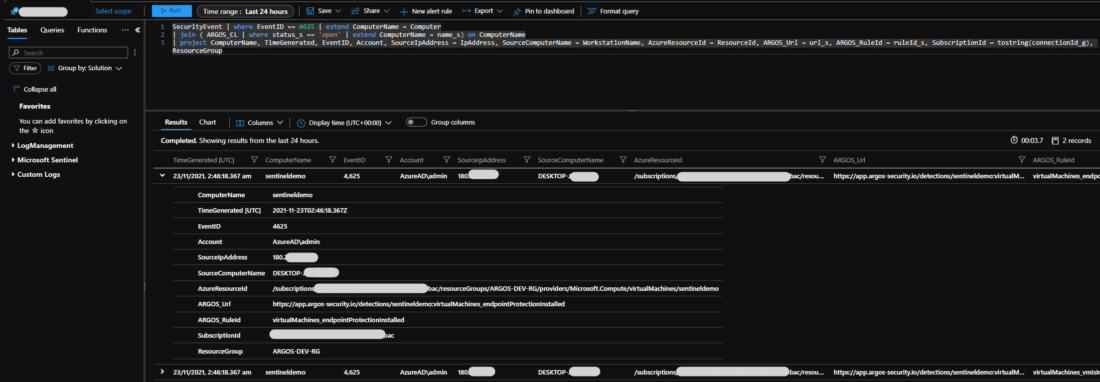 azure Cloud security CSPM
azure Cloud security CSPM
Cloud teams tell us they want to be able to see security issues in their environment in a central location.…
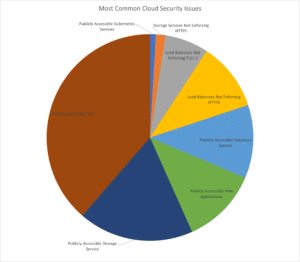 Cloud security
Cloud security
We are coming to the end of 2021, and it is a good time to look at the state of…
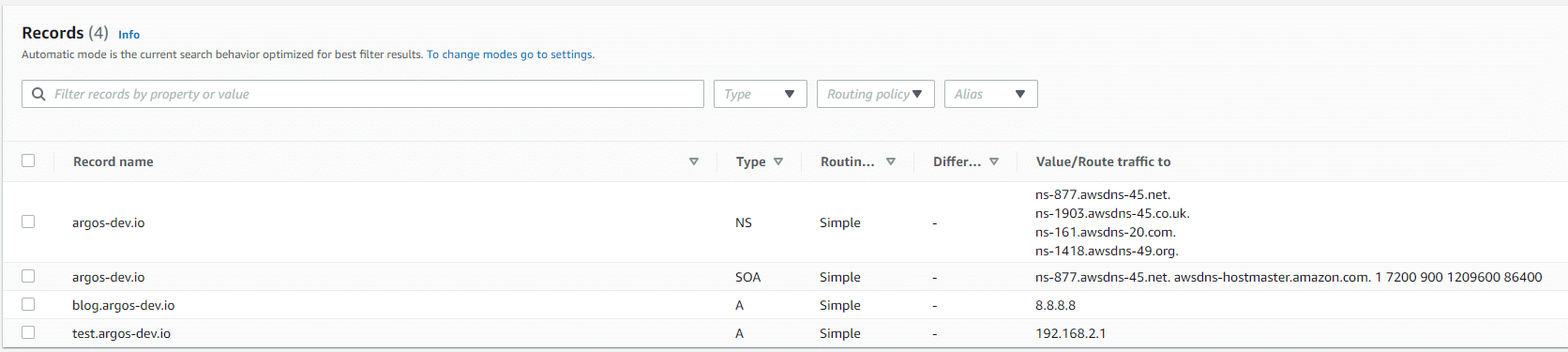 aws Cloud security CSPM
aws Cloud security CSPM
Dangling DNS records are a real security issue and without going into too much detail as to why this is,…
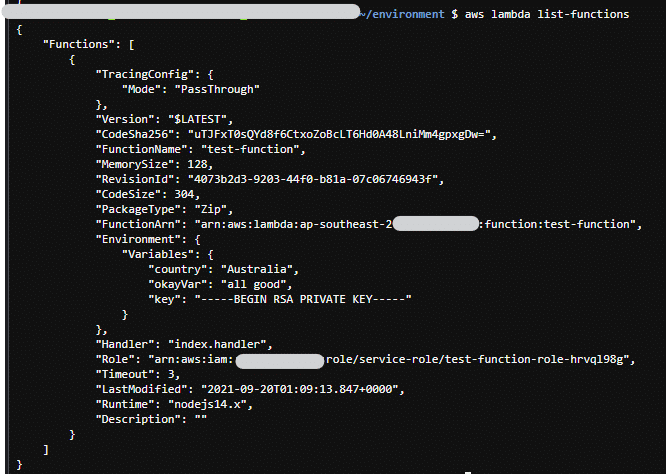 Cloud security CSPM
Cloud security CSPM
AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy,…
