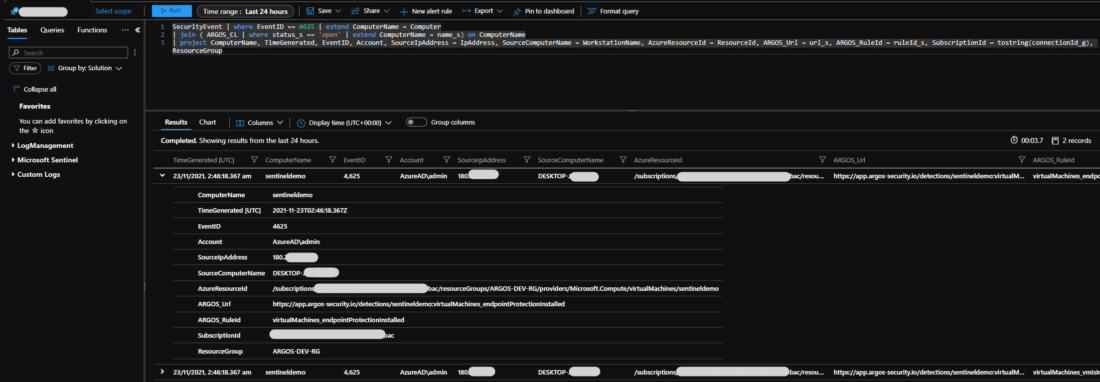
Cloud teams tell us they want to be able to see security issues in their environment in a central location.…
 azure Cloud security CSPM
azure Cloud security CSPM
 azure Cloud security CSPM
azure Cloud security CSPM
Cloud teams tell us they want to be able to see security issues in their environment in a central location.…
 aws Cloud security CSPM
aws Cloud security CSPM
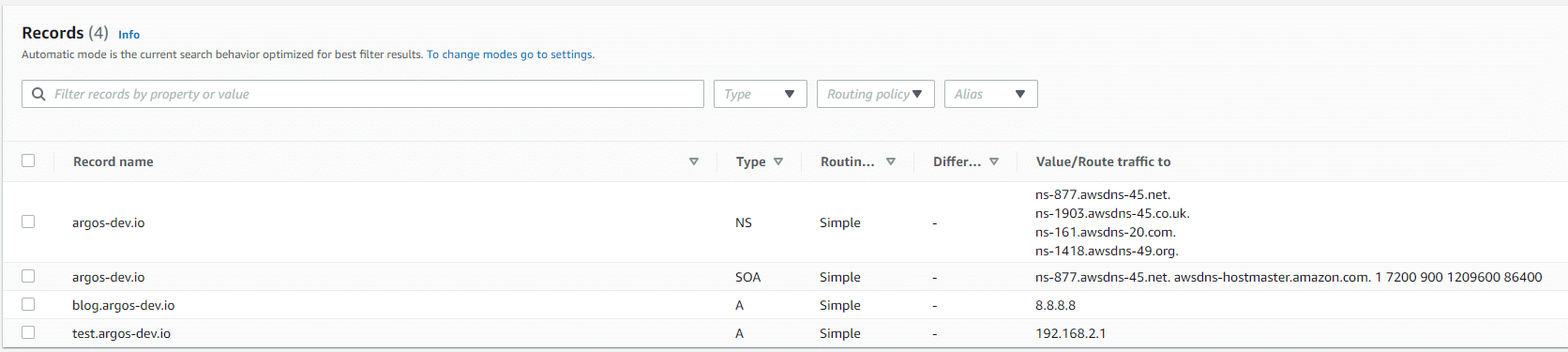
Dangling DNS records are a real security issue and without going into too much detail as to why this is,…
 Cloud security CSPM
Cloud security CSPM
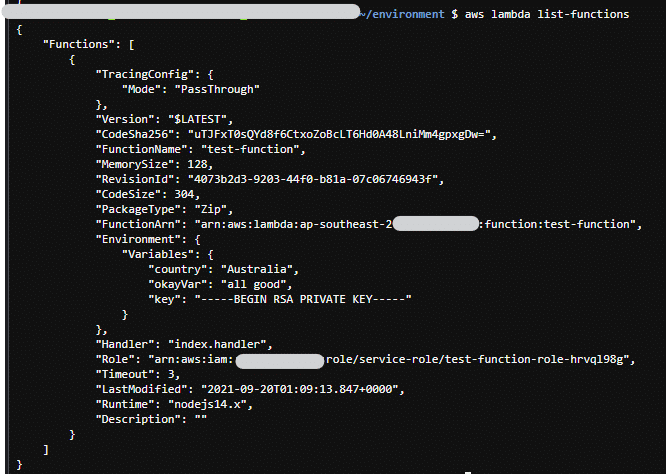
AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy,…
 Cloud security CSPM
Cloud security CSPM
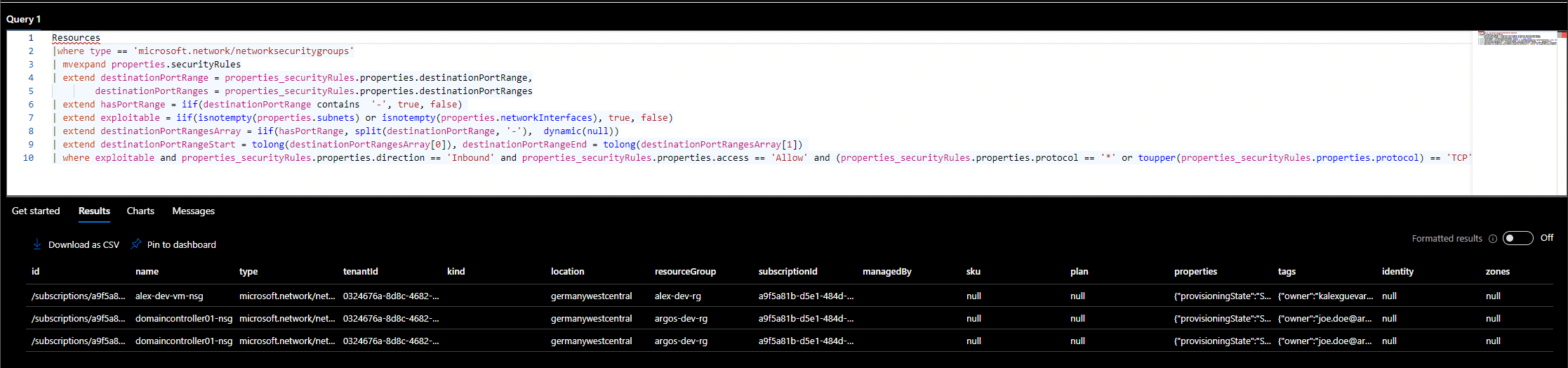
Public Azure Virtual Machines are one of the most exploited resources in the Azure cloud. As we mentioned in our…
One of probably the most commonly referred to services in breaches / data leaks is Amazon AWS’s storage service S3.…
 Cloud security CSPM
Cloud security CSPM
ARGOS has deep insights into our customers’ cloud environments across the three major public clouds providers. There are a handful of common recurring themes when it comes to cloud misconfigurations.
 Cloud security CSPM Devsecops
Cloud security CSPM Devsecops
Why is Cloud Security such a big challenge?
Many organisations seem to struggle with insecure cloud environments even though their Cloud Providers (Microsoft Azure, Amazon AWS, Google GCP) provide them with all the tools they need to create secure platforms.
