Did you come here because you typed “What is CSPM” or “Do I need a CIEM?” into the search engine?…
 aws Cloud security
aws Cloud security
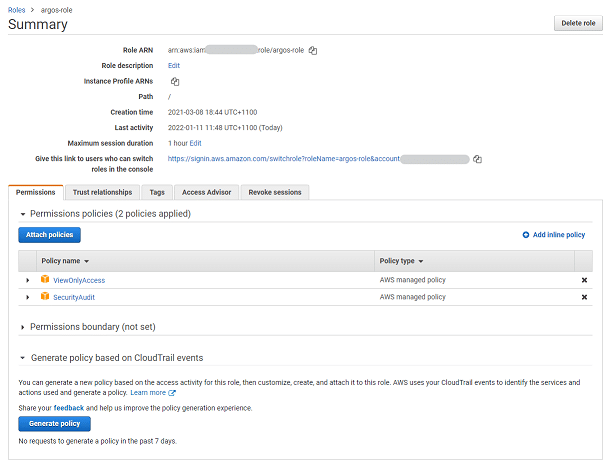
How To Secure an AWS IAM Role by IP Address
Amazon Web Services (AWS) Identity and Access Management (IAM) is one of the things that is often, let’s say, overly…
 azure Cloud security Devsecops
azure Cloud security Devsecops
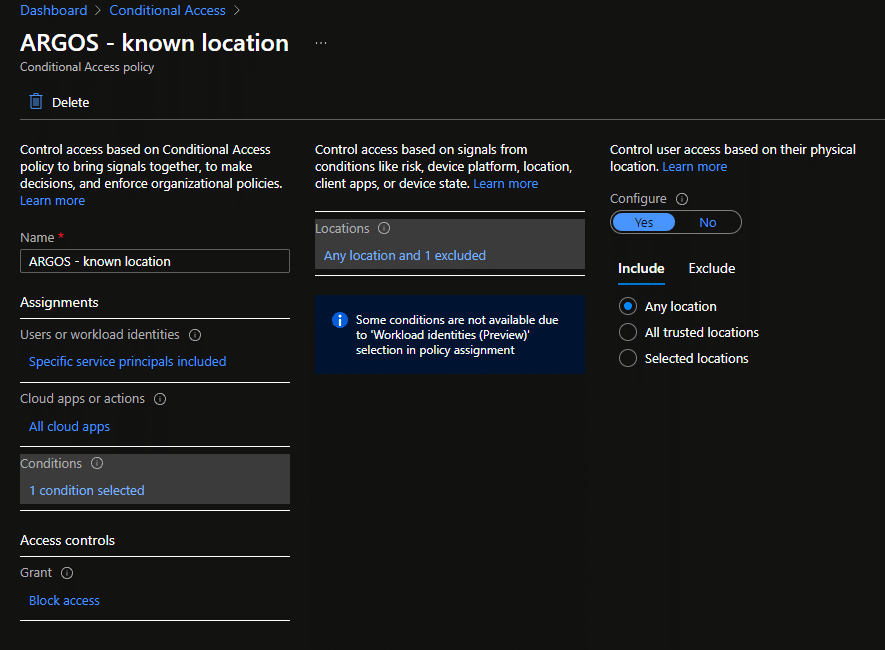
How to Secure an Azure Service Principal with Conditional Access
Identity and Access Management (IAM) is absolutely fundamental to a Cloud operation, however, sometimes you had to make allowances for…
 azure Cloud security CSPM
azure Cloud security CSPM
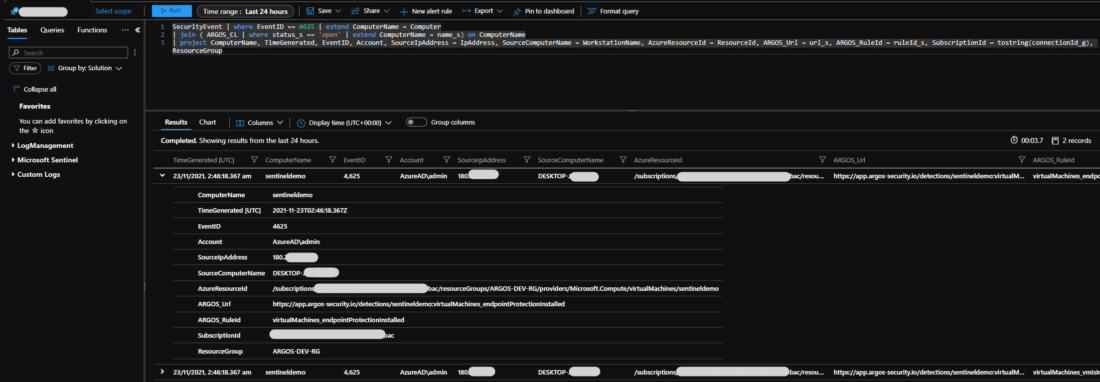
How to Integrate with Microsoft Sentinel SIEM
Cloud teams tell us they want to be able to see security issues in their environment in a central location.…
 Cloud security
Cloud security
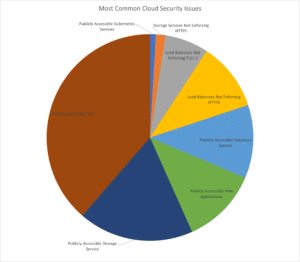
Cloud Security Report 2021
We are coming to the end of 2021, and it is a good time to look at the state of…
 aws Cloud security CSPM
aws Cloud security CSPM
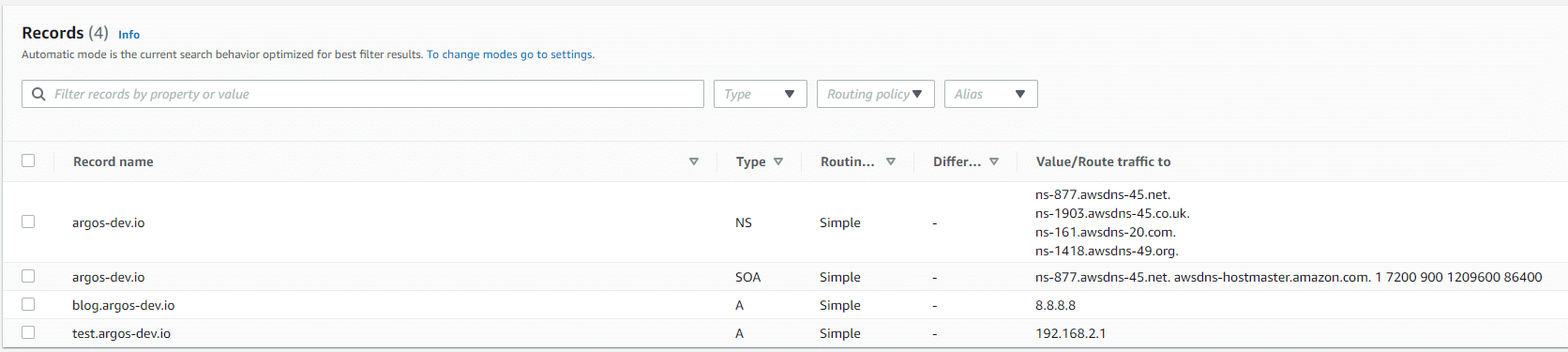
How to Detect Potentially Dangerous Dangling DNS on AWS
Dangling DNS records are a real security issue and without going into too much detail as to why this is,…
 Cloud security CSPM
Cloud security CSPM
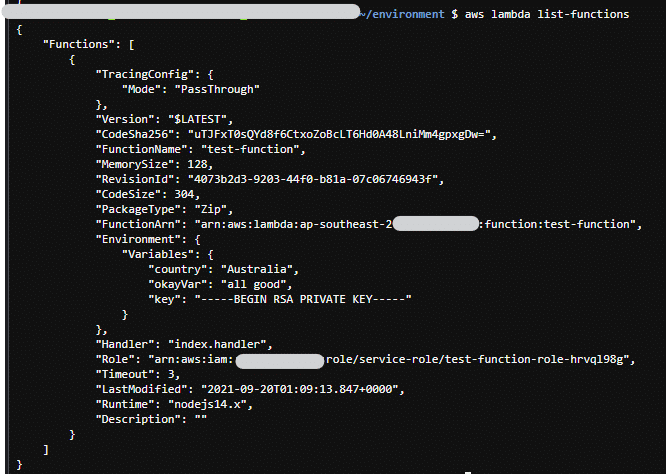
How to Monitor for Secrets in AWS Lambda
AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy,…
 Cloud security CSPM
Cloud security CSPM
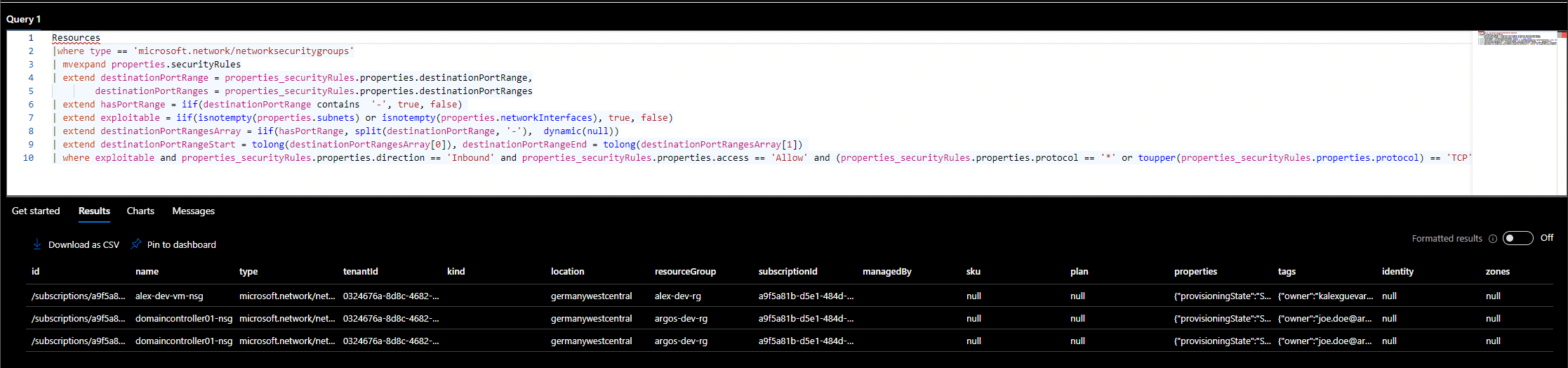
How To Monitor For Risky Public Azure Virtual Machines
Public Azure Virtual Machines are one of the most exploited resources in the Azure cloud. As we mentioned in our…
How to find those stupid & annoying public AWS S3 Buckets
One of probably the most commonly referred to services in breaches / data leaks is Amazon AWS’s storage service S3.…
Azure CosmosDB Vulnerability – What do I need to do?
Just recently Wiz released an announcement into a very critical vulnerability in one of Microsoft Azure’s flagship services, Azure Cosmos DB. Because these…
