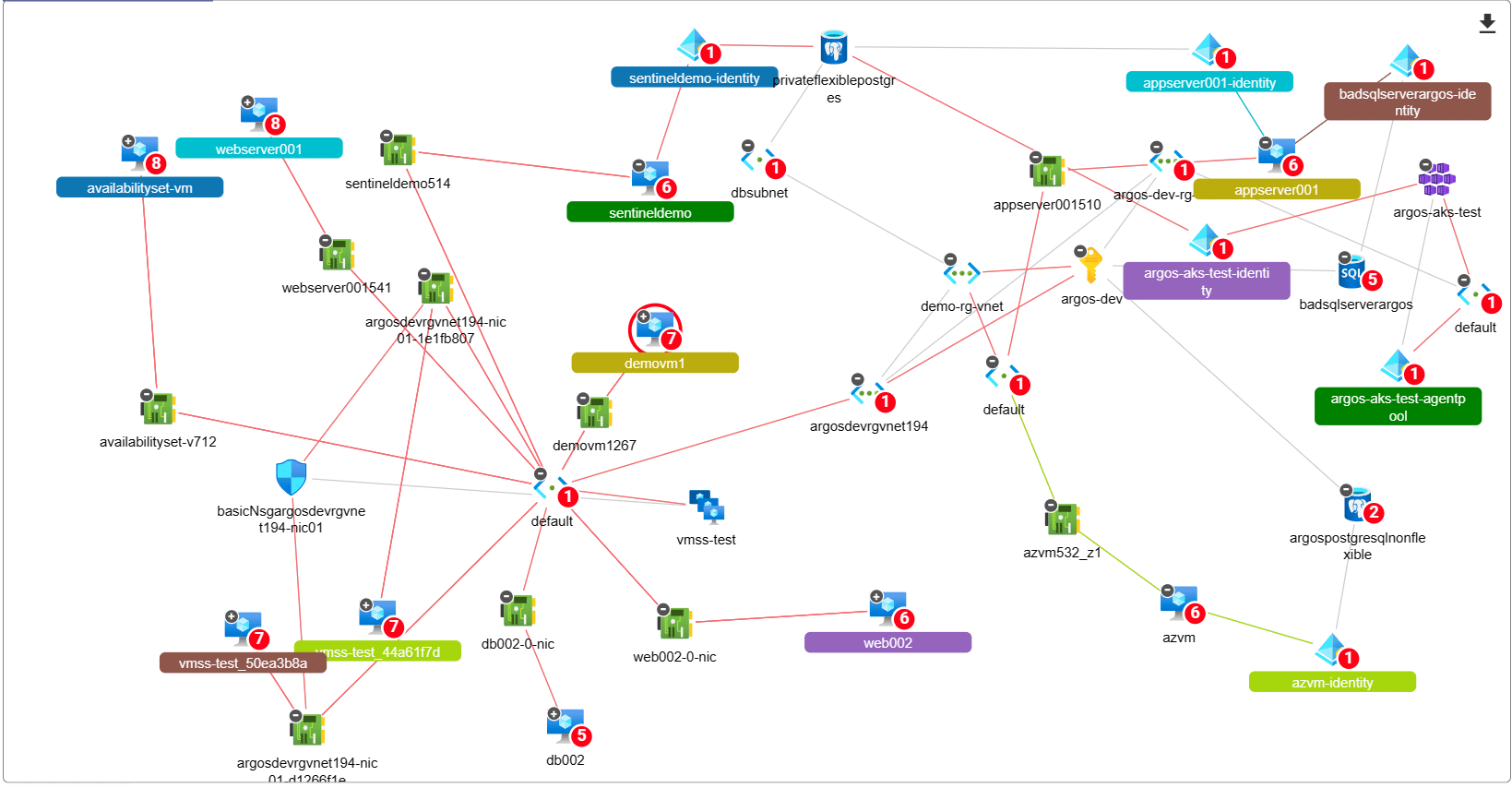
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
 azure Cloud security
azure Cloud security
 azure Cloud security
azure Cloud security
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
 azure Cloud security
azure Cloud security
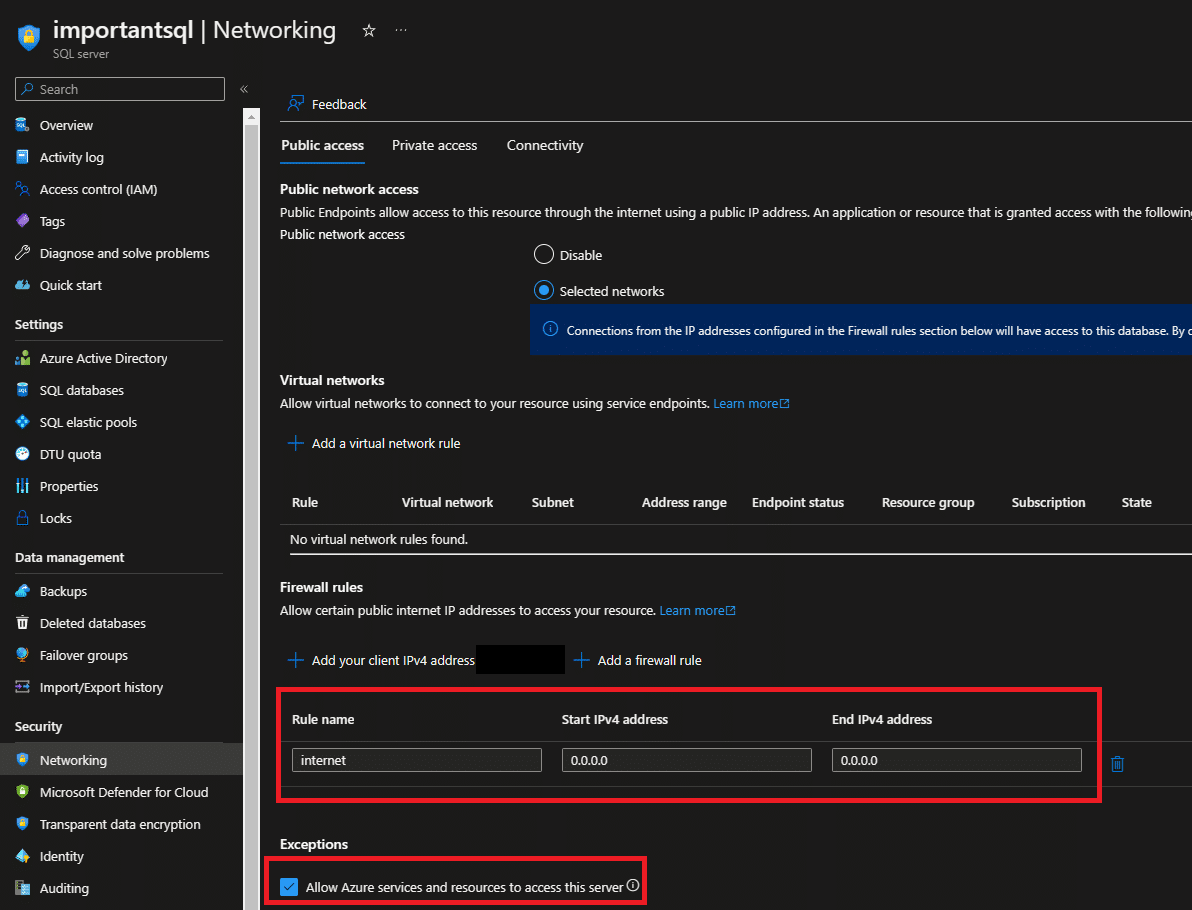
Azure SQL is a cloud-based relational database management system that is widely used by businesses and organizations around the world.…
 azure Cloud security
azure Cloud security
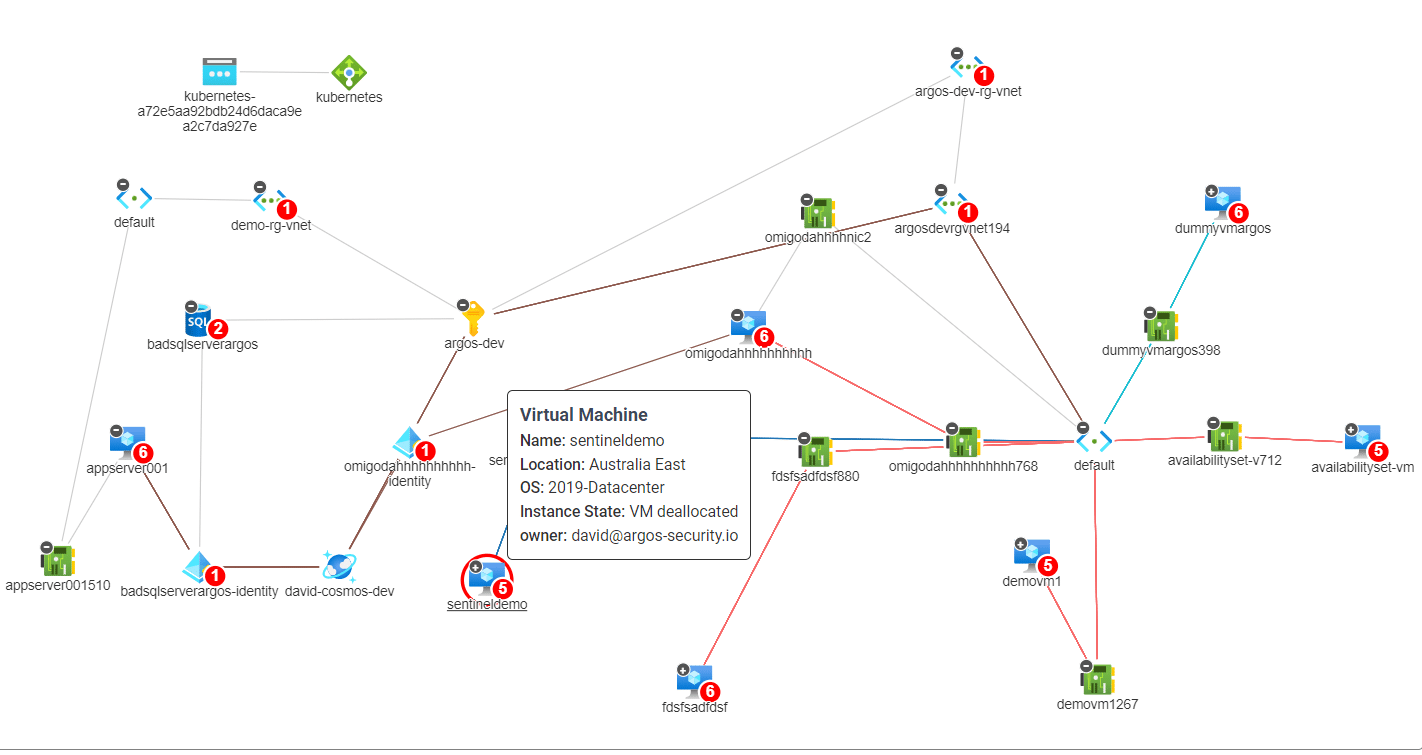
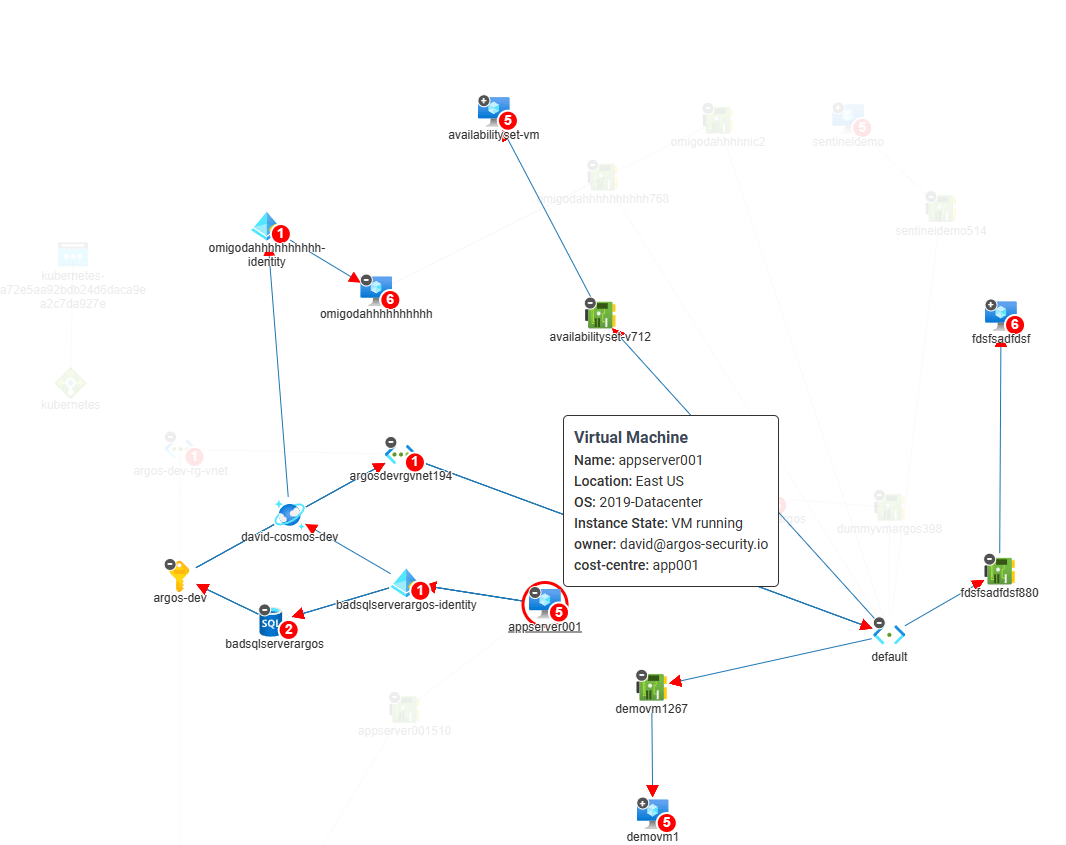
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 Cloud security Start up
Cloud security Start up
Today, we wanted to give you a little history lesson into why we started ARGOS. What lead us to build…
Did you come here because you typed “What is CSPM” or “Do I need a CIEM?” into the search engine?…
 Cloud security CSPM
Cloud security CSPM
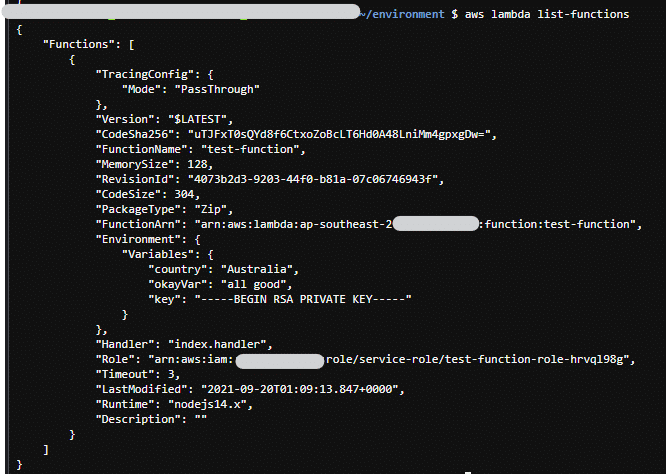
AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy,…
 Cloud security CSPM
Cloud security CSPM
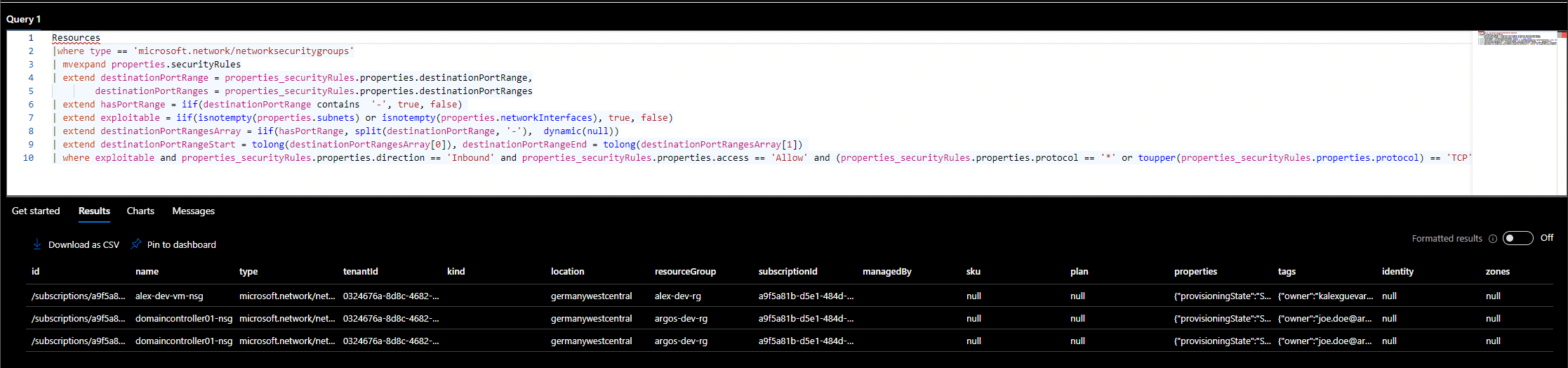
Public Azure Virtual Machines are one of the most exploited resources in the Azure cloud. As we mentioned in our…
One of probably the most commonly referred to services in breaches / data leaks is Amazon AWS’s storage service S3.…
 Cloud security Development
Cloud security Development
A very common feature request over the last few months was to enable people in the ARGOS ecosystem to write custom functionality against our APIs. Initially this was not possible as we did not expose our APIs for direct consumption.
