Quite regularly teams need to create Entra ID App Registrations. One use case might be the onboarding of a SaaS…
 azure Cloud security
azure Cloud security
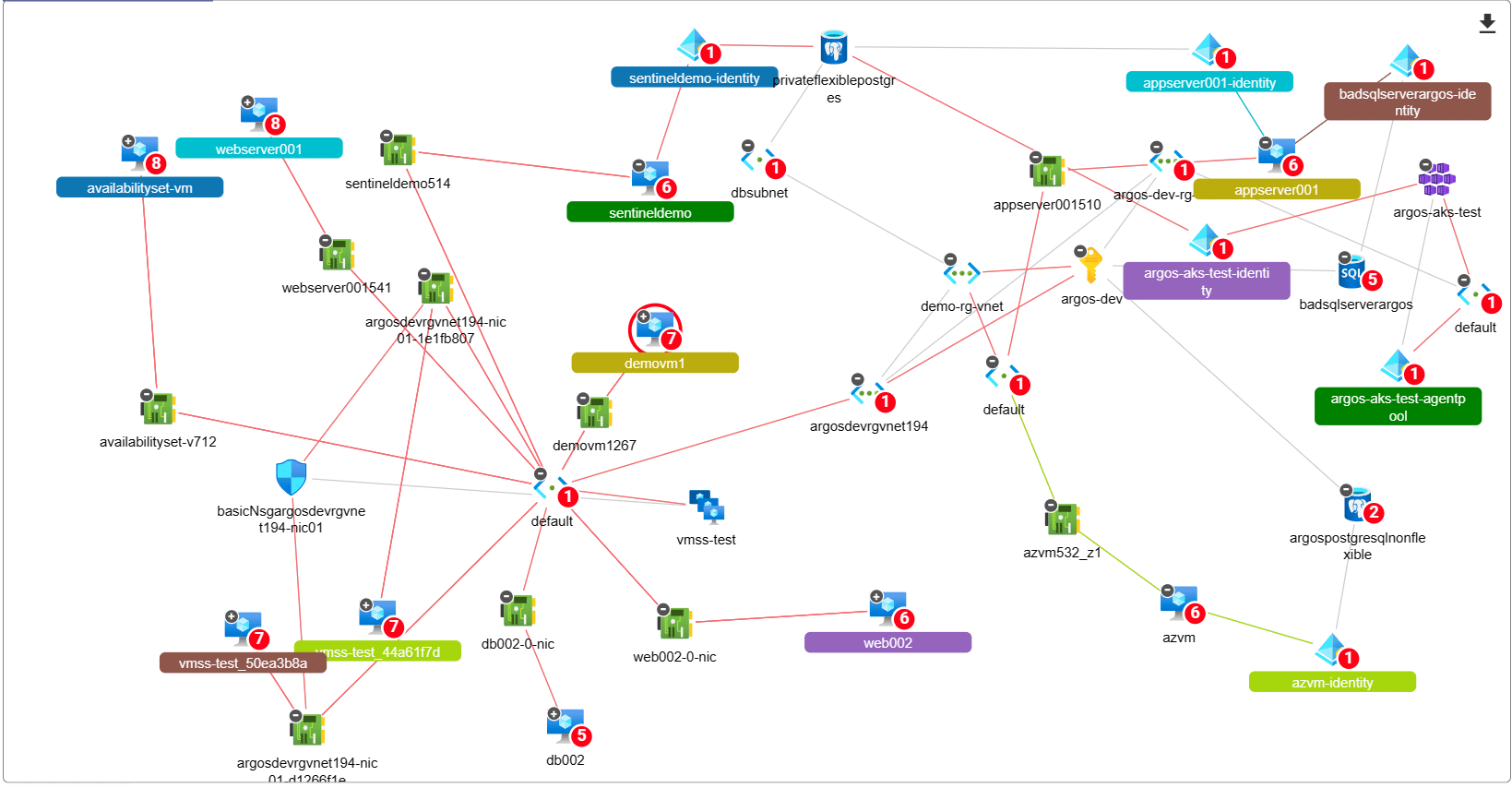
Discovering Attack Paths in Microsoft Azure for Enhanced Security
We’re changing the way consultants assess Azure Subscriptions and detect Attack Paths. All you need is “Reader” access to an…
 azure Cloud security
azure Cloud security
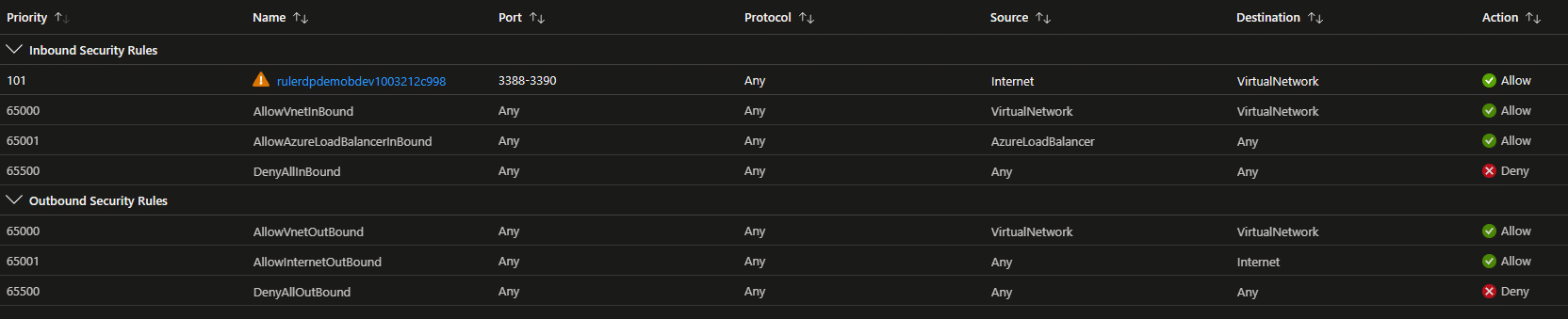
Top 5 Azure VM Security Blunders That Get You Owned
Top 5 Azure VM Security Blunders that will get you owned As more and more businesses embrace Azure Virtual Machines…
 azure Cloud security
azure Cloud security
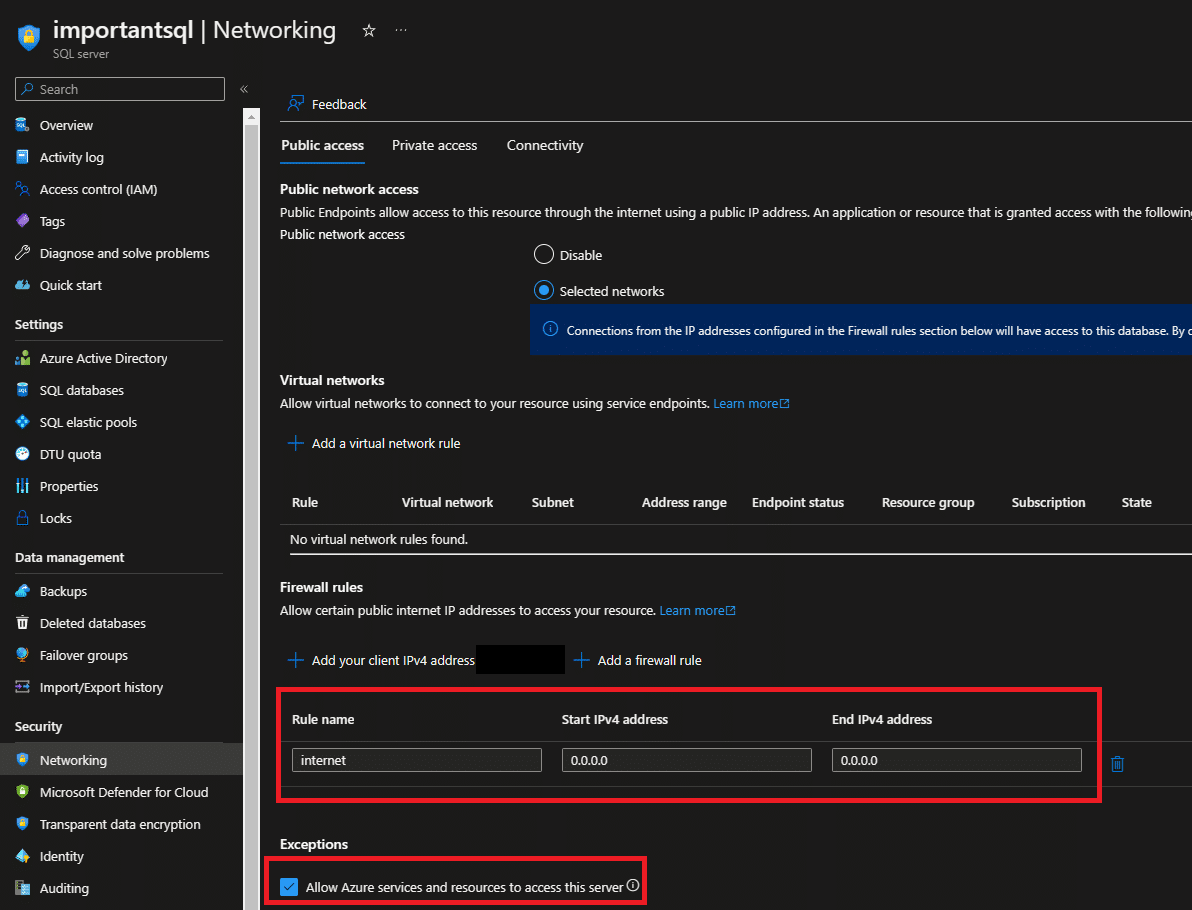
Is Your Azure SQL at Risk? Learn How to Secure It with this Step-by-Step Guide
Azure SQL is a cloud-based relational database management system that is widely used by businesses and organizations around the world.…
 azure Cloud security
azure Cloud security
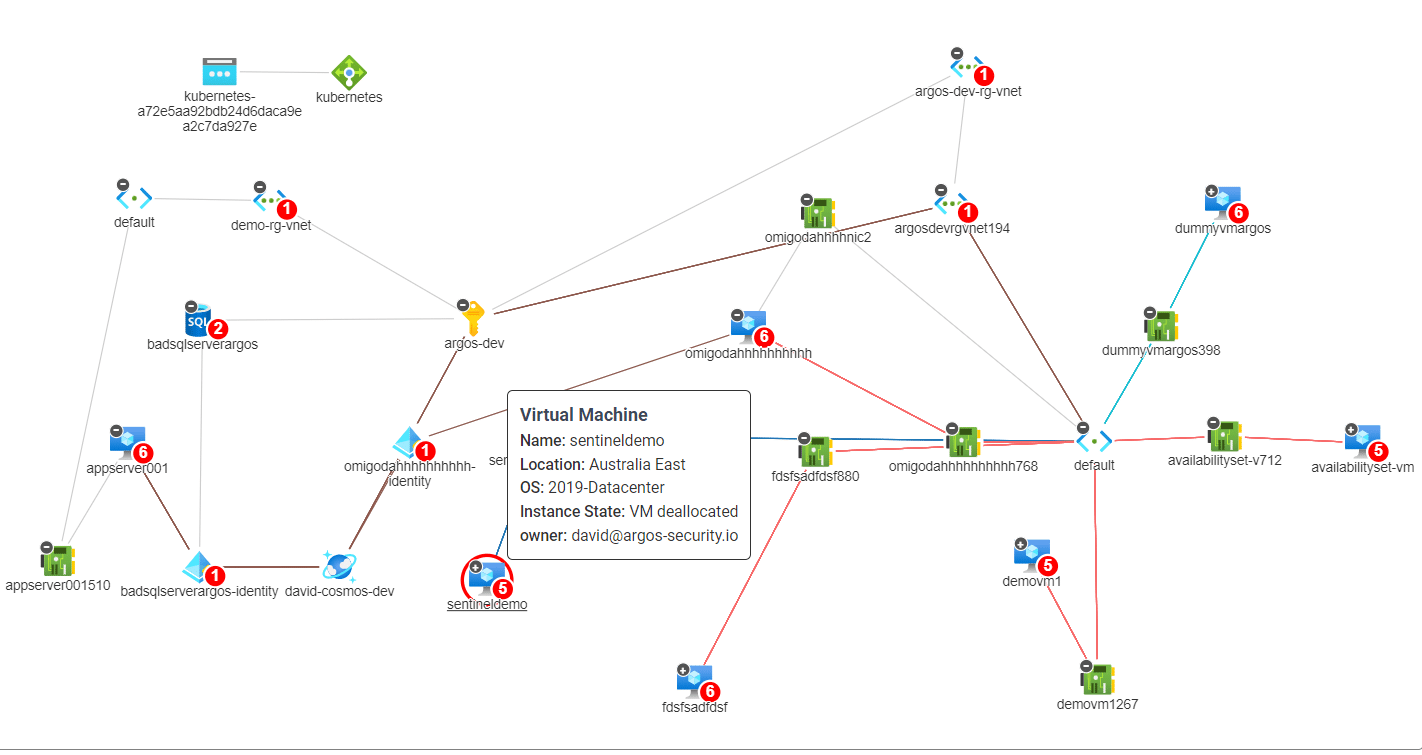
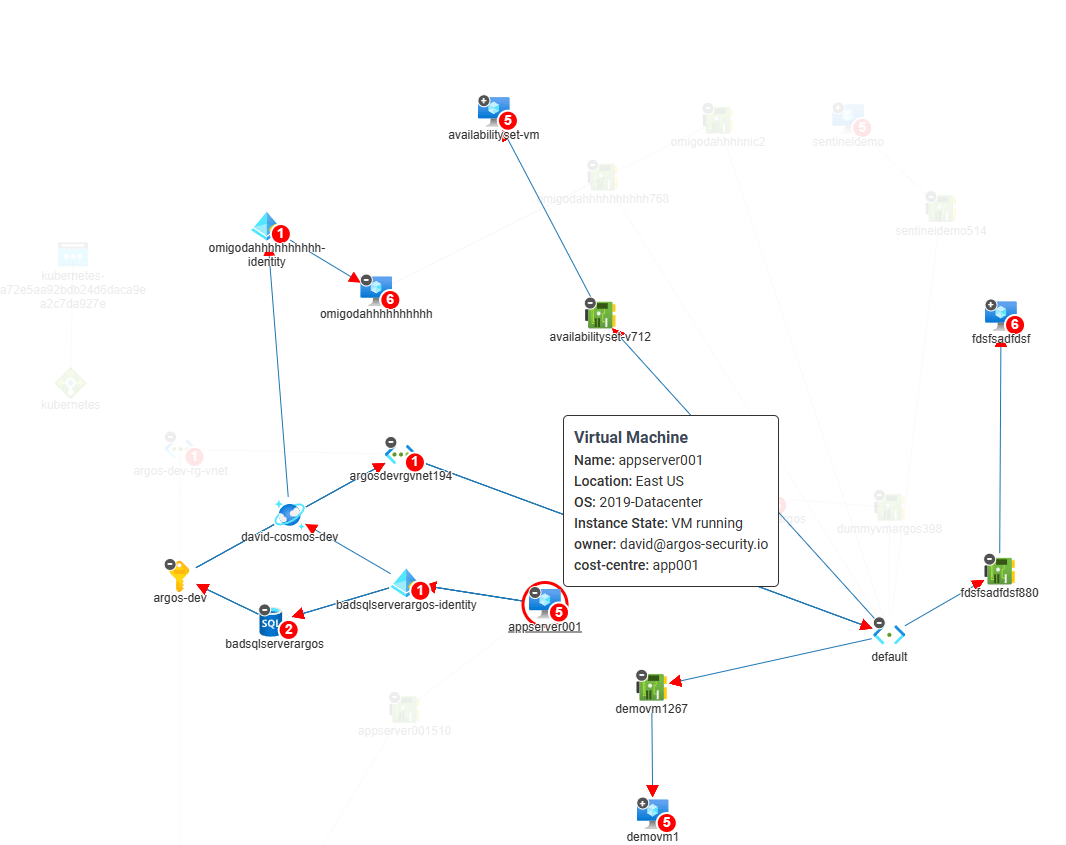
Identifying and Securing Hidden Attack Paths in Azure Infrastructure
Lateral movement attacks are a significant risk facing organizations that operate in the cloud. These attacks occur when an attacker…
 Cloud security Start up
Cloud security Start up
Why We Started ARGOS – Cloud Security FOR Consultants
Today, we wanted to give you a little history lesson into why we started ARGOS. What lead us to build…
How to make sense of CSPM, CAASM, CIEM, CNAPP
Did you come here because you typed “What is CSPM” or “Do I need a CIEM?” into the search engine?…
 aws Cloud security CSPM
aws Cloud security CSPM
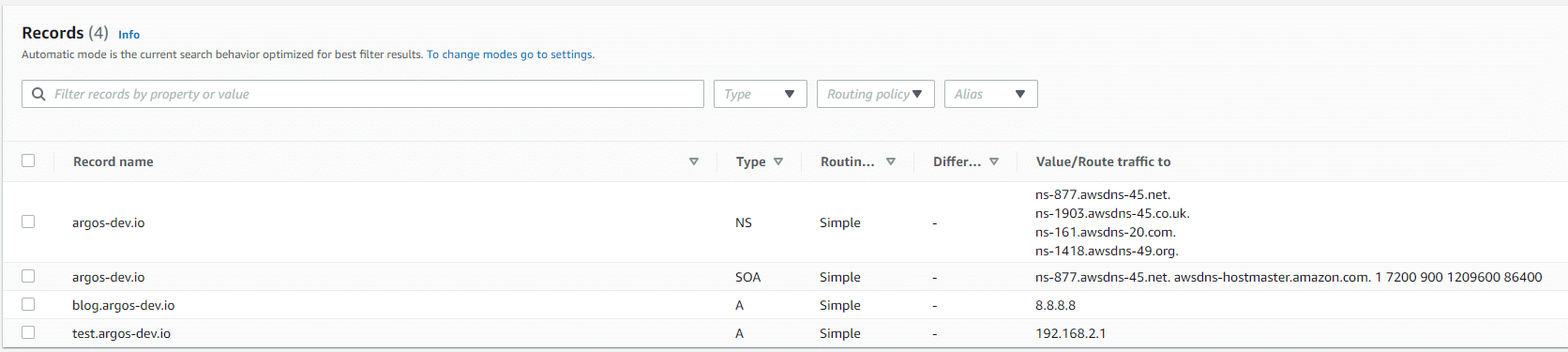
How to Detect Potentially Dangerous Dangling DNS on AWS
Dangling DNS records are a real security issue and without going into too much detail as to why this is,…
 Cloud security CSPM
Cloud security CSPM
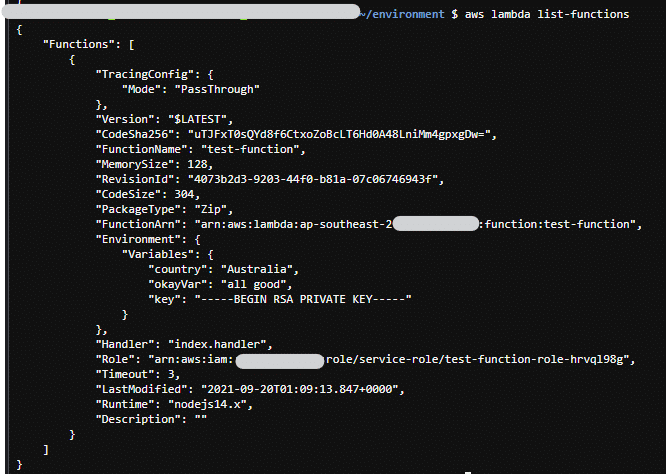
How to Monitor for Secrets in AWS Lambda
AWS Lambda Functions have been, are and will be a major part of most AWS implementations. They are super handy,…
 Cloud security CSPM
Cloud security CSPM
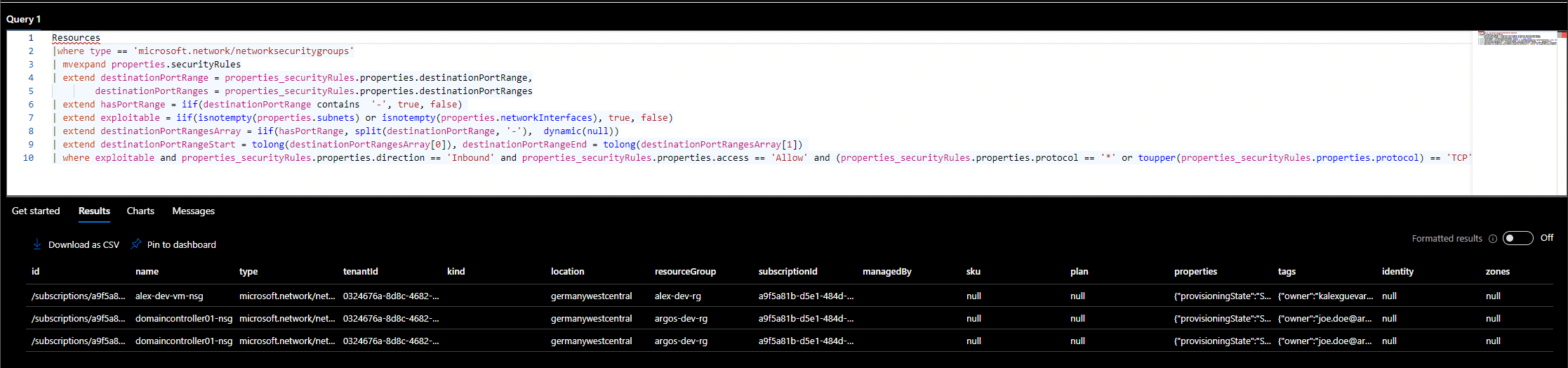
How To Monitor For Risky Public Azure Virtual Machines
Public Azure Virtual Machines are one of the most exploited resources in the Azure cloud. As we mentioned in our…
